If you’re new to Aztec—welcome. This is the rundown on Aztec: what it is, how it works and why it matters.
Without solving privacy at the base layer, networks remain exposed—no matter what’s built on top. Patchwork solutions like centralized sequencers, trusted execution environments, or mixers may sound credible, but they fall short. And when privacy breaks, everything on-chain is at risk: identities, accounts, assets, even institutions. We all know that privacy can’t be an add-on. It has to be native, end-to-end, from the start. It needs to be flexible, easy to code, fast to execute and affordable to scale.
No native privacy.
No real use cases.
No real adoption.
No real impact.
See the big picture. This diagram illustrates how Aztec efficiently processes both public and private functions in a single hybrid transaction.
The Ignition Chain launched late last year, as the first fully decentralized L2 on Ethereum– a huge milestone for decentralized networks. The team has reinvented what true programmable privacy means, building the execution model from the ground up— combining the programmability of Ethereum with the privacy of Zcash in a single execution environment.
Since then, the network has been running with zero downtime with 3,500+ sequencers and 50+ provers across five continents. With the infrastructure now in place, the network is fully in the hands of the community, and the culmination of the past 8 years of work is now converging.
Major upgrades have landed across four tracks: the execution layer, the proving system, the programming language, Noir, and the decentralization stack. Together, these milestones deliver on Aztec’s original promise, a system where developers can write fully programmable smart contracts with customizable privacy.
The infrastructure is in place. The code is ready. And we’re ready to ship.
The execution layer delivers on Aztec's core promise: fully programmable, privacy-preserving smart contracts on Ethereum.
A complete dual state model is now in place–with both private and public state. Private functions execute client-side in the Private Execution Environment (PXE), running directly in the user's browser and generating zero-knowledge proofs locally, so that private data never leaves the original device. Public functions execute on the Aztec Virtual Machine (AVM) on the network side.
Aztec.js is now live, giving developers a full SDK for managing accounts and interacting with contracts. Native account abstraction has been implemented, meaning every account is a smart contract with customizable authentication rules. Note discovery has been solved through a tagging mechanism, allowing recipients to efficiently query for relevant notes without downloading and decrypting everything on the network.
Contract standards are underway, with the Wonderland team delivering AIP-20 for tokens and AIP-721 for NFTs, along with escrow contracts and logic libraries, providing the production-ready building blocks for the Alpha Network.
The proving system is what makes Aztec's privacy guarantees real, and it has deep roots.
In 2019, Aztec's cofounder Zac Williamson and Chief Scientist Ariel Gabizon introduced PLONK, which became one of the most widely used proving systems in zero-knowledge cryptography. Since then, Aztec's cryptographic backend, Barretenberg, has evolved through multiple generations, each facilitating faster, lighter, and more efficient proving than the last. The latest innovation, CHONK (Client-side Highly Optimized ploNK), is purpose-built for proving on phones and browsers and is what powers proof generation for the Alpha Network.
CHONK is a major leap forward for the user experience, dramatically reducing the memory and time required to generate proofs on consumer devices. It leverages best-in-class circuit primitives, a HyperNova-style folding scheme for efficiently processing chains of private function calls, and Goblin, a hyper-efficient purpose-built recursion acceleration scheme. The result is that private transactions can be proven on the devices people actually use, not just powerful servers.
This matters because privacy on Aztec means proofs are generated on the user's own device, keeping private data private. If proving is too slow or too resource-intensive, privacy becomes impractical. CHONK makes it practical.
Decentralization is what makes Aztec's privacy guarantees credible. Without it, a central operator could censor transactions, introduce backdoors, or compromise user privacy at will.
Aztec addressed this by hardcoding decentralized sequencing, proving, and governance directly into the base protocol. The Ignition Chain has proven the stability of this consensus layer, maintaining zero downtime with over 3,500 sequencers and 50+ provers running across five continents. Aztec Labs and the Aztec Foundation run no sequencers and do not participate in governance.
Noir 1.0 is nearing completion, bringing a stable, production-grade language within reach. Aztec's own protocol circuits have been entirely rewritten in Noir, meaning the language is already battle-tested at the deepest layer of the stack.
Internal and external audits of the compiler and toolchain are progressing in parallel, and security tooling including fuzzers and bytecode parsers is nearly finished. A stable, audited language means application teams can build on Alpha with confidence that the foundation beneath them won't shift.
The code for Alpha Network, a functionally complete and raw version of the network, is ready.
The Alpha Network brings fully programmable, privacy-preserving smart contracts to Ethereum for the first time. It's the culmination of years of parallel work across the four tracks in the Aztec Roadmap. Together, they enable efficient client-side proofs that power customizable smart contracts, letting users choose exactly what stays private and what goes public.
No other project in the space is close to shipping this.
The code is written. The network is running. All the pieces are in place. The governance proposal is now live on the forum and open for discussion. Read through it, ask questions, poke holes, and help shape the path forward.
Once the community is aligned, the proposal moves to a vote. This is how a decentralized network upgrades. Not by a team pushing a button, but by the people running it.
Programmable privacy will unlock a renaissance in onchain adoption. Real-world applications are coming and institutions are paying attention. Alpha represents the culmination of eight years of intense work to deliver privacy on Ethereum.
Now it needs to be battle-tested in the wild.
View the updated product roadmap here and join us on Thursday, March 5th, at 3 pm UTC on X to hear more about the most recent updates to our product roadmap.
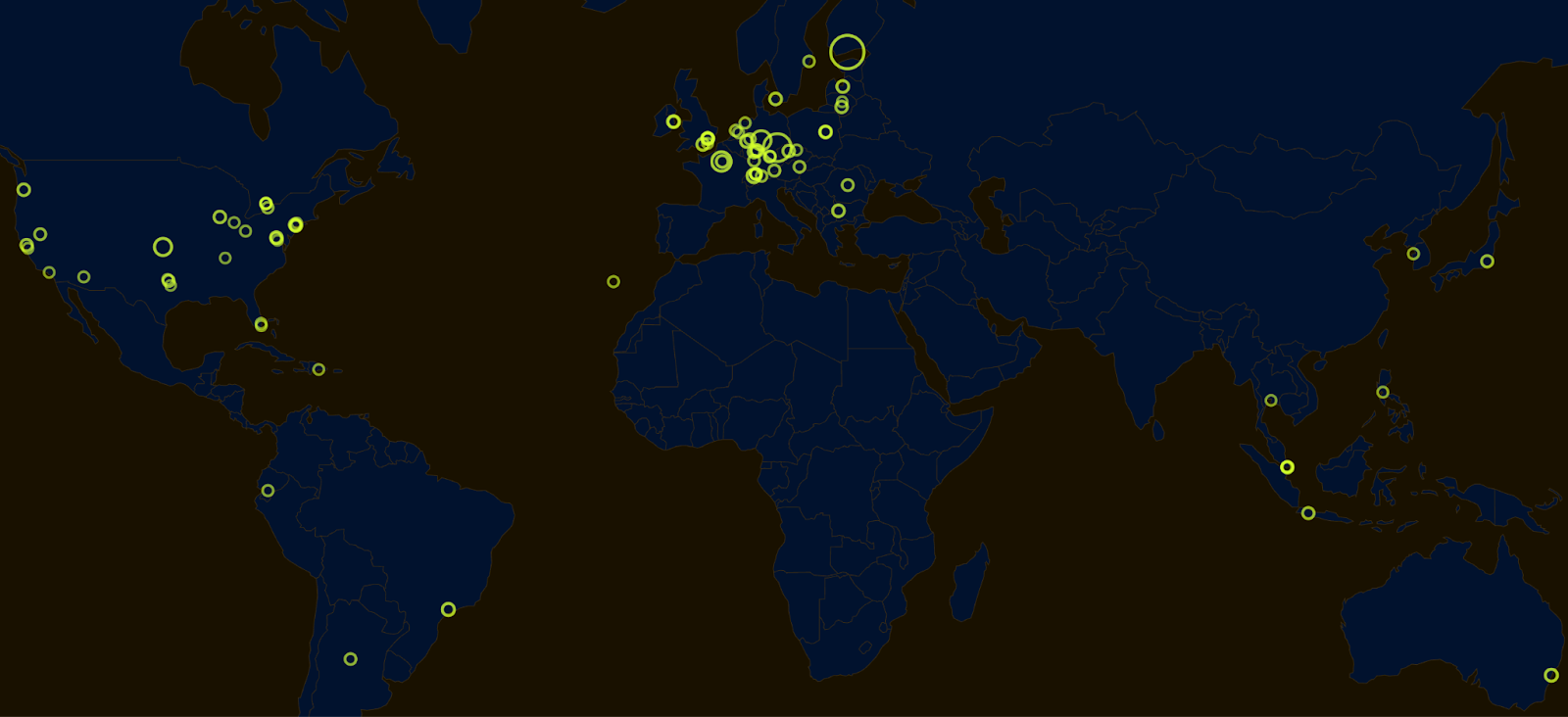
In November 2025, the Aztec Ignition Chain went live as the first decentralized L2 on Ethereum. Since launch, more than 185 operators across 5 continents have joined the network, with 3,400+ sequencers now running. The Ignition Chain is the backbone of the Aztec Network; true end-to-end programmable privacy is only possible when the underlying network is decentralized and permissionless.
Until now, only participants from the $AZTEC token sale have been able to stake and earn block rewards ahead of Aztec's upcoming Token Generation Event (TGE), but that's about to change. Keep reading for an update on the state of the network and learn how you can spin up your own sequencer or start delegating your tokens to stake once TGE goes live.
The Ignition Chain launched to prove the stability of the consensus layer before the execution environment ships, which will enable privacy-preserving smart contracts. The network has remained healthy, crossing a block height of 75k blocks with zero downtime. That includes navigating Ethereum's major Fusaka upgrade in December 2025 and a governance upgrade to increase the queue speed for joining the sequencer set.
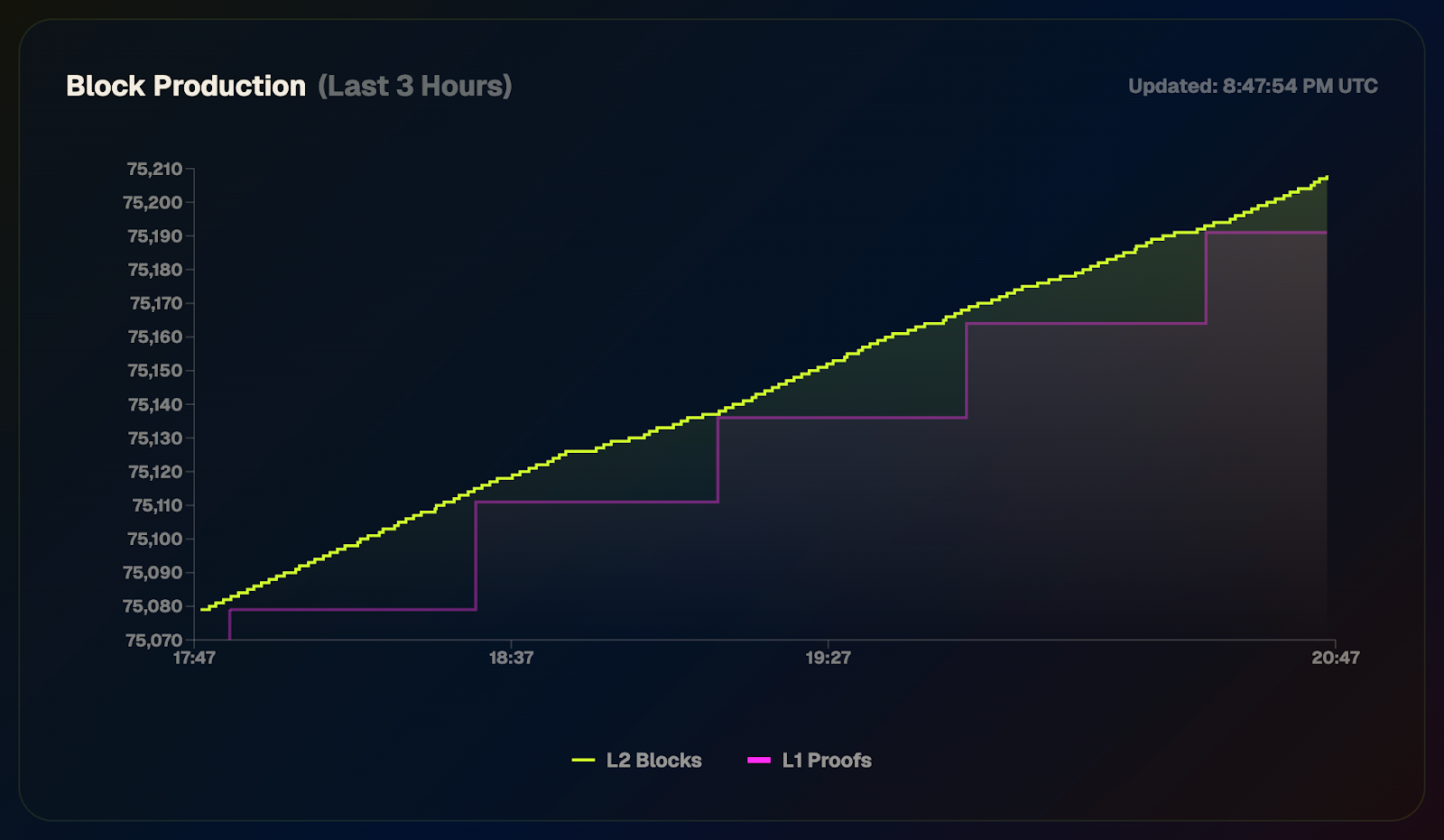
Over 30M $AZTEC tokens have been distributed to sequencers and provers to date. Block rewards go out every epoch (every 32 blocks), with 70% going to sequencers and 30% going to provers for generating block proofs.
If you don't want to run your own node, you can delegate your stake and share in block rewards through the staking dashboard. Note that fractional staking is not currently supported, so you'll need 200k $AZTEC tokens to stake.
The Ignition Chain launched as a decentralized network from day one. The Aztec Labs and Aztec Foundation teams are not running any sequencers on the network or participating in governance. This is your network.
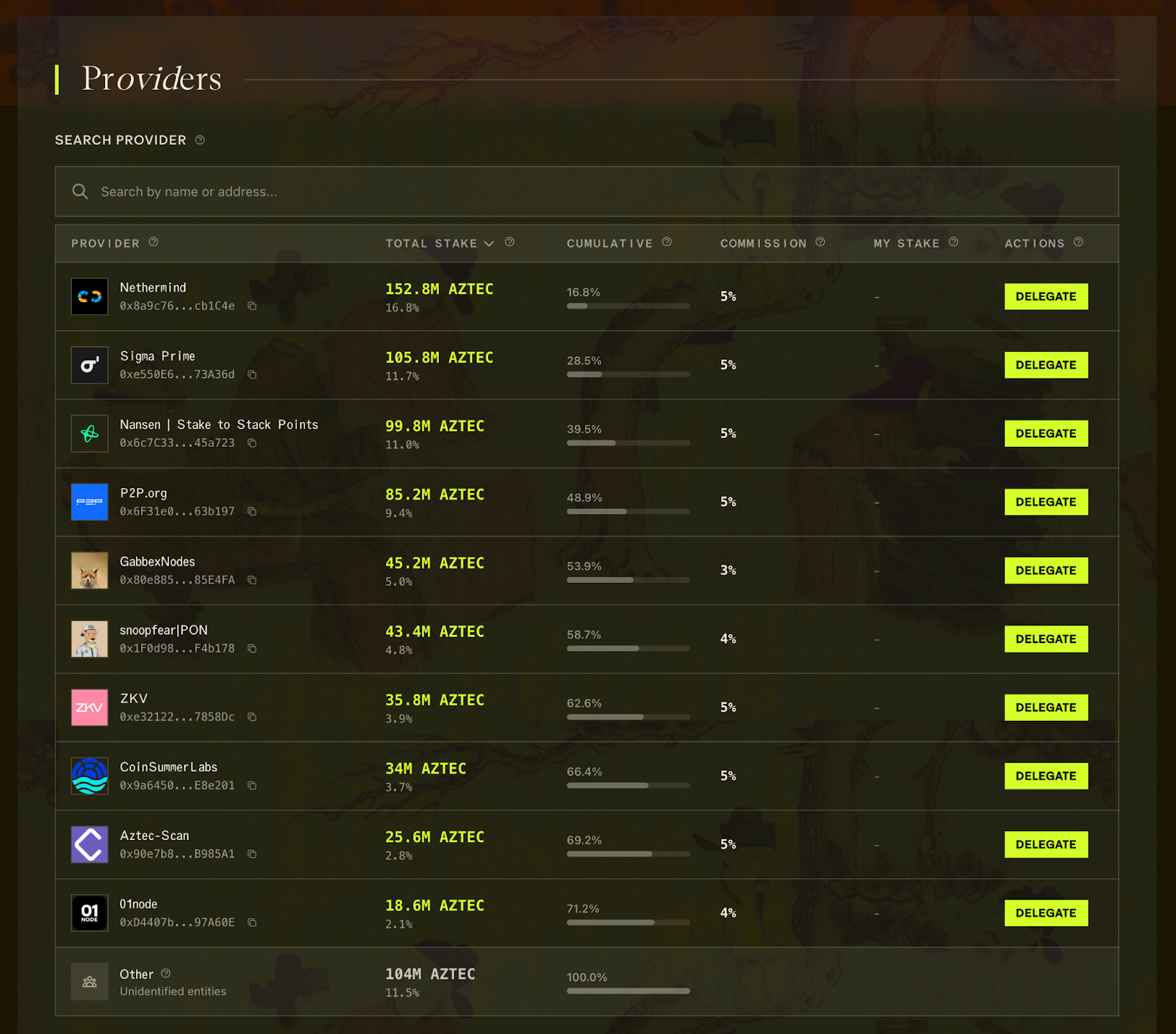
Anyone who purchased 200k+ tokens in the token sale can stake or delegate their tokens on the staking dashboard. Over 180 operators are now running sequencers, with more joining daily as they enter the sequencer set from the queue. And it's not just sequencers: 50+ provers have joined the permissionless, decentralized prover network to generate block proofs.
These operators span the globe, from solo stakers to data centers, from Australia to Portugal.
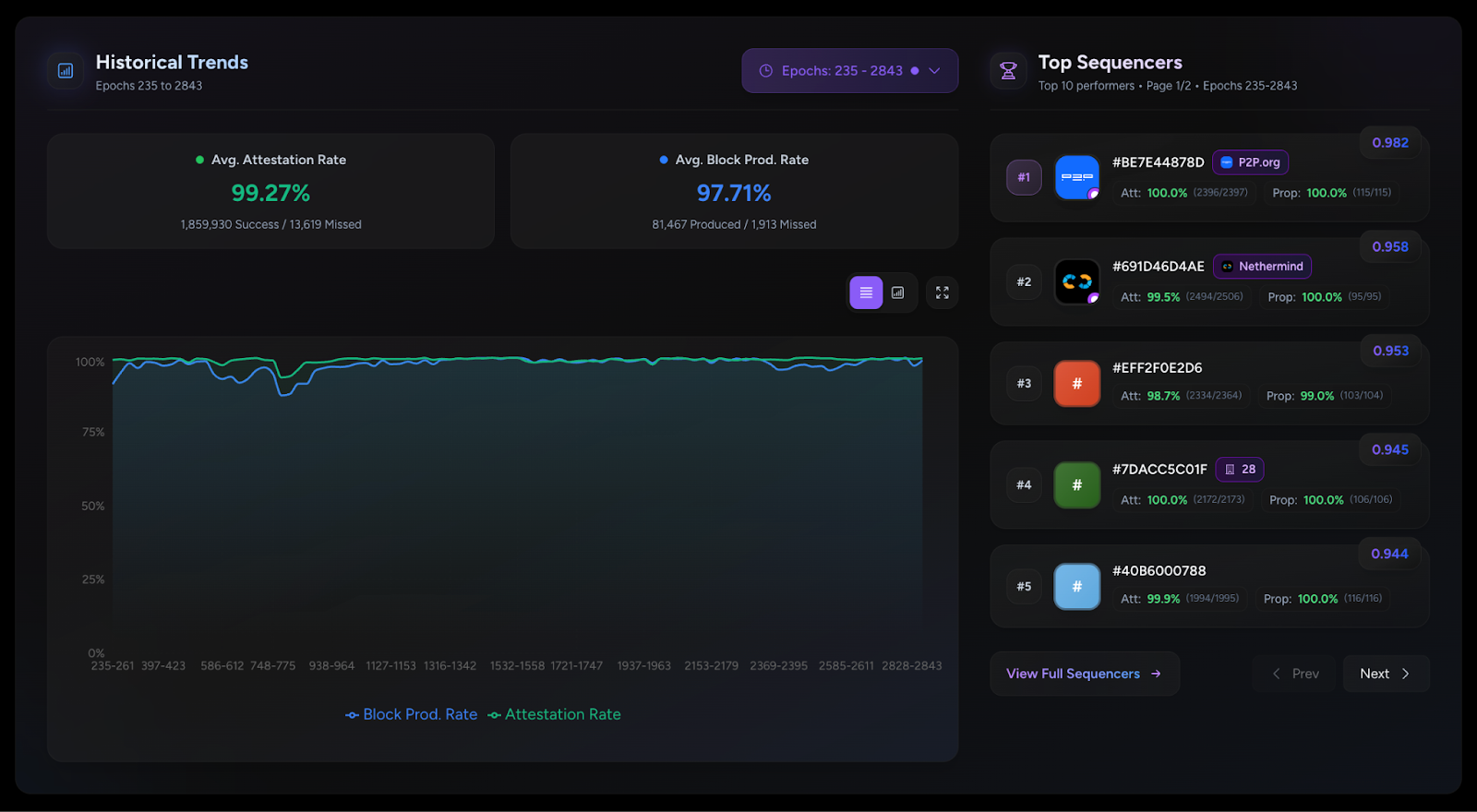
Participating sequencers have maintained a 99%+ attestation rate since network launch, demonstrating strong commitment and network health. Top performers include P2P.org, Nethermind, and ZKV. You can see all block activity and staker performance on the Dashtec dashboard.
On January 26th, 2026, the community passed a governance proposal for TGE. This makes tokens tradable and unlocks the AZTEC/ETH Uniswap pool as early as February 11, 2026. Once that happens, anyone with 200k $AZTEC tokens can run a sequencer or delegate their stake to participate in block rewards.
Here's what you need to run a validator node:
These are accessible specs for most solo stakers. If you've run an Ethereum validator before, you're already well-equipped.
To get started, head to the Aztec docs for step-by-step instructions on setting up your node. You can also join the Discord to connect with other operators, ask questions, and get support from the community. Whether you run your own hardware or delegate to an experienced operator, you're helping build the infrastructure for a privacy-preserving future.
Solo stakers are the beating heart of the Aztec Network. Welcome aboard.
The $AZTEC token sale was the first of its kind, conducted entirely onchain with ~50% of the capital committed coming from the community. The sale was conducted completely onchain to ensure that you have control over your tokens from day one. As we approach the TGE vote, all token sale participants will be able to vote to unlock their tokens and make them tradable.
Immediately following the $AZTEC token sale, tokens could be withdrawn from the sale website into your personal Token Vault smart contracts on the Ethereum mainnet. Right now, token holders are not able to transfer or trade these tokens.
The TGE is a governance vote that decides when to unlock these tokens. If the vote passes, three things happen:
This decision is entirely in the hands of $AZTEC token holders. The Aztec Labs and Aztec Foundation teams, and investors cannot participate in staking or governance for 12 months, which includes the TGE governance proposal. Team and investor tokens will also remain locked for 1 year and then slowly unlock over the next 2 years.
The proposal for TGE is now live, and sequencers are already signaling to bring the proposal to a vote. Once enough sequencers have signaled, anyone who participated in the token sale will be able to connect their Token Vault contract to the governance dashboard to vote. Note, this will require you to stake/unstake and follow the regular 15-day process to withdraw tokens.
If the vote passes, TGE can go live as early as February 12, 2026, at 7am UTC. TGE can be executed by the first person to call the execute function to execute the proposal after the time above.
If you participated in the token sale, you don't have to do anything if you prefer not to vote. If the vote passes, your tokens will become available to trade at TGE. If you want to vote, the process happens in two phases:
Sequencers kick things off by signaling their support. Once 600 out of 1,000 sequencers signal, the proposal moves to a community vote.
After sequencers create the proposal, all Token Vault holders can vote using the voting governance dashboard. Please note that anyone who wants to vote must stake their tokens, locking their tokens for at least 15 days to ensure the proposal can be executed before the voter exits. Once signaling is complete, the timeline is as follows:
Vote Requirements:
Do I need to participate in the vote? No. If you don't vote, your tokens will become available for trading when TGE goes live.
Can I vote if I have less than 200,000 tokens? Yes! Anyone who participated in the token sale can participate in the TGE vote. You'll need to connect your wallet to the governance dashboard to vote.
Is there a withdrawal period for my tokens after I vote? Yes. If you participate in the vote, you will need to withdraw your tokens after voting. Voters can initiate a withdrawal of their tokens immediately after voting, but require a standard 15-day withdrawal period to ensure the vote is executed before voters can exit.
If I have over 200,000 tokens is additional action required to make my tokens tradable after TGE? Yes. If you purchased over 200,000 $AZTEC tokens, you will need to stake your tokens before they become tradable.
What if the vote fails? A new proposal can be submitted. Your tokens remain locked until a successful vote is completed, or the fallback date of November 13, 2026, whichever happens first.
I'm a Genesis sequencer. Does this apply to me? Genesis sequencer tokens cannot be unlocked early. You must wait until November 13, 2026, to withdraw. However, you can still influence the vote by signaling, earn block rewards, and benefit from trading being enabled.
This overview covers the essentials, but the full technical proposal includes contract addresses, code details, and step-by-step instructions for sequencers and advanced users.
Read the complete proposal on the Aztec Forum and join us for the Privacy Rabbit Hole on Discord happening this Thursday, January 22, 2026, at 15:00 UTC.
Follow Aztec on X to stay up to date on the latest developments.
The $AZTEC token sale was conducted entirely onchain to maximize transparency and fair distribution. Next steps for holders are as follows:
The $AZTEC token sale has come to a close– the sale was conducted entirely onchain, and the power is now in your hands. Over 16.7k people participated, with 19,476 ETH raised. A huge thank you to our community and everyone who participated– you all really showed up for privacy. 50% of the capital committed has come from the community of users, testnet operators and creators!
Now that you have your tokens, what’s next? This guide walks you through the next steps leading up to TGE, showing you how to withdraw, stake, and vote with your tokens.
The $AZTEC sale was conducted onchain to ensure that you have control over your own tokens from day 1 (even before tokens become transferable at TGE).
The team has no control over your tokens. You will be self-custodying them in a smart contract known as the Token Vault on the Ethereum mainnet ahead of TGE.
Your Token Vault contract will:
To create and withdraw your tokens to your Token Vault, simply go to the sale website and click on ‘Create Token Vault.’ Any unused ETH from your bids will be returned to your wallet in the process of creating your Token Vault.
If you have 200,000+ tokens, you are eligible to start staking and earning block rewards today.
You can stake by connecting your Token Vault to the staking dashboard, just select a provider to delegate your stake. Alternatively, you can run your own sequencer node.
If your Token Vault holds 200,000+ tokens, you must stake in order to withdraw your tokens after TGE. If your Token Vault holds less than 200,000 tokens, you can withdraw without any additional steps at TGE
Fractional staking for anyone with less than 200,000 tokens is not currently supported, but multiple external projects are already working to offer this in the future.
TGE is triggered by an onchain governance vote, which can happen as early as February 11th, 2026.
At TGE, 100% of tokens from the token sale will be transferable. Only token sale participants and genesis sequencers can participate in the TGE vote, and only tokens purchased in the sale will become transferrable.
Community members discuss potential votes on the governance forum. If the community agrees, sequencers signal to start a vote with their block proposals. Once enough sequencers agree, the vote goes onchain for eligible token holders.
Voting lasts 7 days, requires participation of at least 100,000,000 $AZTEC tokens, and passes if 2/3 vote yes.
Following a successful yes vote, anyone can execute the proposal after a 7-day execution delay, triggering TGE.
At TGE, the following tokens will be 100% unlocked and available for trading:
Join us Thursday, December 11th at 3 pm UTC for the next Discord Town Hall–AMA style on next steps for token holders. Follow Aztec on X to stay up to date on the latest developments.
Builders are breaking new ground with Aztec’s unique functionality. This rising cadre is reshaping commerce, culture and everything in between.








Aztec is a fully decentralized, privacy-preserving L2 on Ethereum. It’s a zk rollup that combines Ethereum’s security with cutting-edge cryptography to give users control over what’s public and what stays private. Think of it as the bridge between the transparency of Ethereum and the privacy you need to build real-world applications, like private accounts, transactions, and data.
Aztec is for anyone who values both decentralization and privacy. It serves everyday crypto users who don’t want their entire wallet history exposed. It empowers DeFi builders creating the next generation of private applications. It provides investors and institutions with the ability to conduct confidential transactions or hold private on-chain assets. And it enables stablecoin issuers who want to issue private stablecoins.
Aztec is the only decentralized blockchain that offers full end-to-end programmable privacy. Aztec lets you build entire applications — DeFi, gaming, identity, voting — where privacy isn’t an afterthought, it’s the default. By using client-site zero-knowledge proofs, Aztec ensures your balances, activity, and even contract execution remain confidential while still inheriting Ethereum’s security.
Most blockchains are fully transparent — anyone can see your balances, trades, and on-chain history. Aztec flips this model by being a privacy blockchain that gives users choice: make things public when needed, keep everything else private. Unlike other privacy crypto projects that run their own chains, Aztec is a zk rollup L2 on Ethereum. That means it has Ethereum’s security, composability, and community — plus programmable end-to-end privacy.
Noir is Aztec’s programming language for zero-knowledge applications. It lets developers build apps that blend public and private elements without needing to understand complex cryptography. For everyday users, this means apps built on Aztec just work — private by default, but flexible when something needs to be public. Developers write smart contracts using aztec.nr, a framework for Noir.
On Aztec, you can trade and lend in DeFi without revealing your wallet balances, vote on proposals privately while still displaying public results, and share data selectively—for example, proving you’re over 18 without disclosing your exact birthday. You can also build private applications for gaming, identity, or financial privacy, and extend Aztec’s privacy features cross-chain into other networks.
Yes. Aztec decentralizes across three layers: sequencers, which order transactions and propose blocks; provers, which generate zk proof for blocks; and governance, where the community decides on upgrades. This structure ensures that Aztec is censorship-resistant and not controlled by a single party—a critical factor for any privacy-preserving blockchain.