

The first decentralized L2 on Ethereum reaches 75k block height with 30M $AZTEC distributed through block rewards.
In November 2025, the Aztec Ignition Chain went live as the first decentralized L2 on Ethereum. Since launch, more than 185 operators across 5 continents have joined the network, with 3,400+ sequencers now running. The Ignition Chain is the backbone of the Aztec Network; true end-to-end programmable privacy is only possible when the underlying network is decentralized and permissionless.
Until now, only participants from the $AZTEC token sale have been able to stake and earn block rewards ahead of Aztec's upcoming Token Generation Event (TGE), but that's about to change. Keep reading for an update on the state of the network and learn how you can spin up your own sequencer or start delegating your tokens to stake once TGE goes live.
The Ignition Chain launched to prove the stability of the consensus layer before the execution environment ships, which will enable privacy-preserving smart contracts. The network has remained healthy, crossing a block height of 75k blocks with zero downtime. That includes navigating Ethereum's major Fusaka upgrade in December 2025 and a governance upgrade to increase the queue speed for joining the sequencer set.
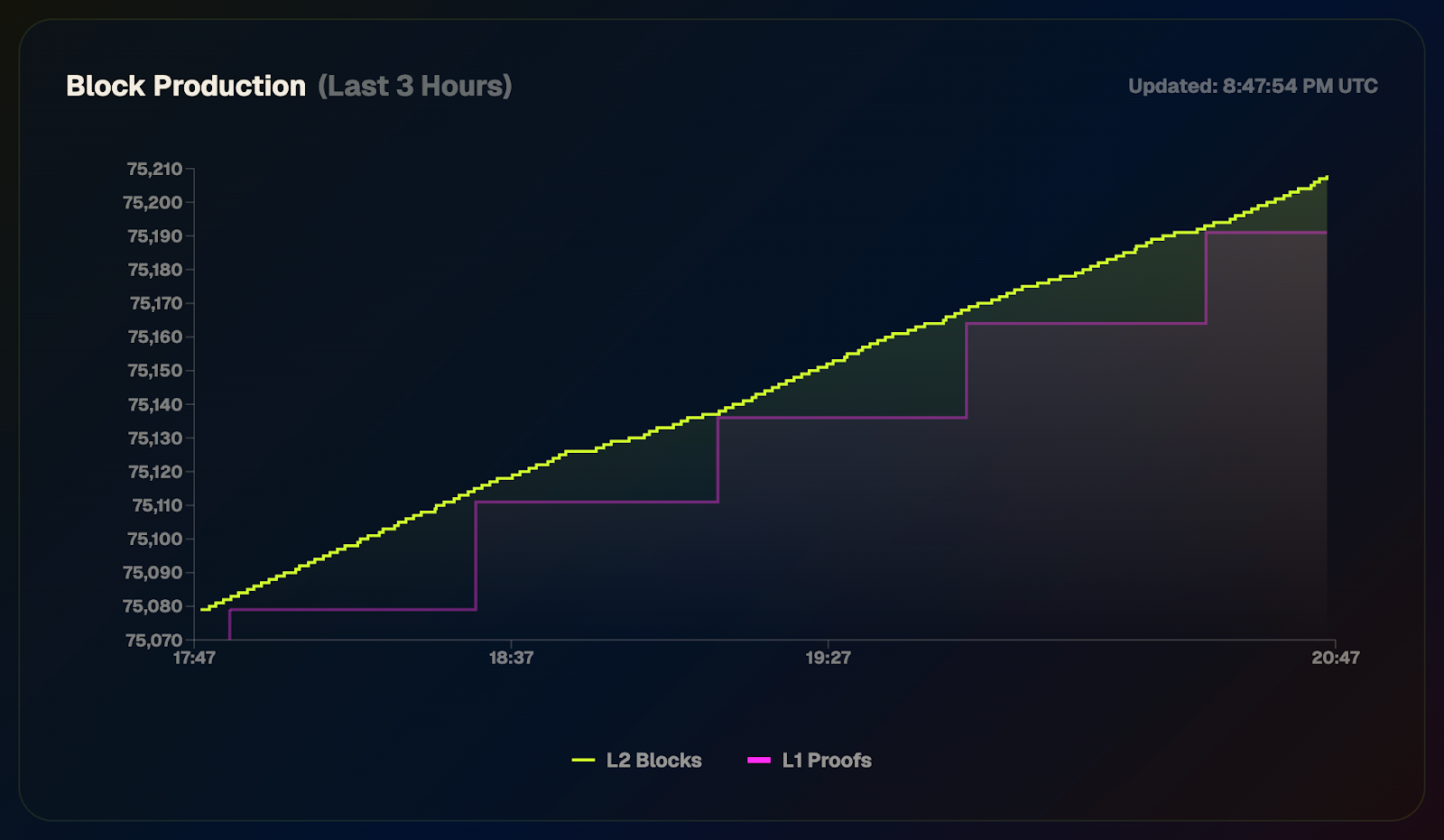
Over 30M $AZTEC tokens have been distributed to sequencers and provers to date. Block rewards go out every epoch (every 32 blocks), with 70% going to sequencers and 30% going to provers for generating block proofs.
If you don't want to run your own node, you can delegate your stake and share in block rewards through the staking dashboard. Note that fractional staking is not currently supported, so you'll need 200k $AZTEC tokens to stake.
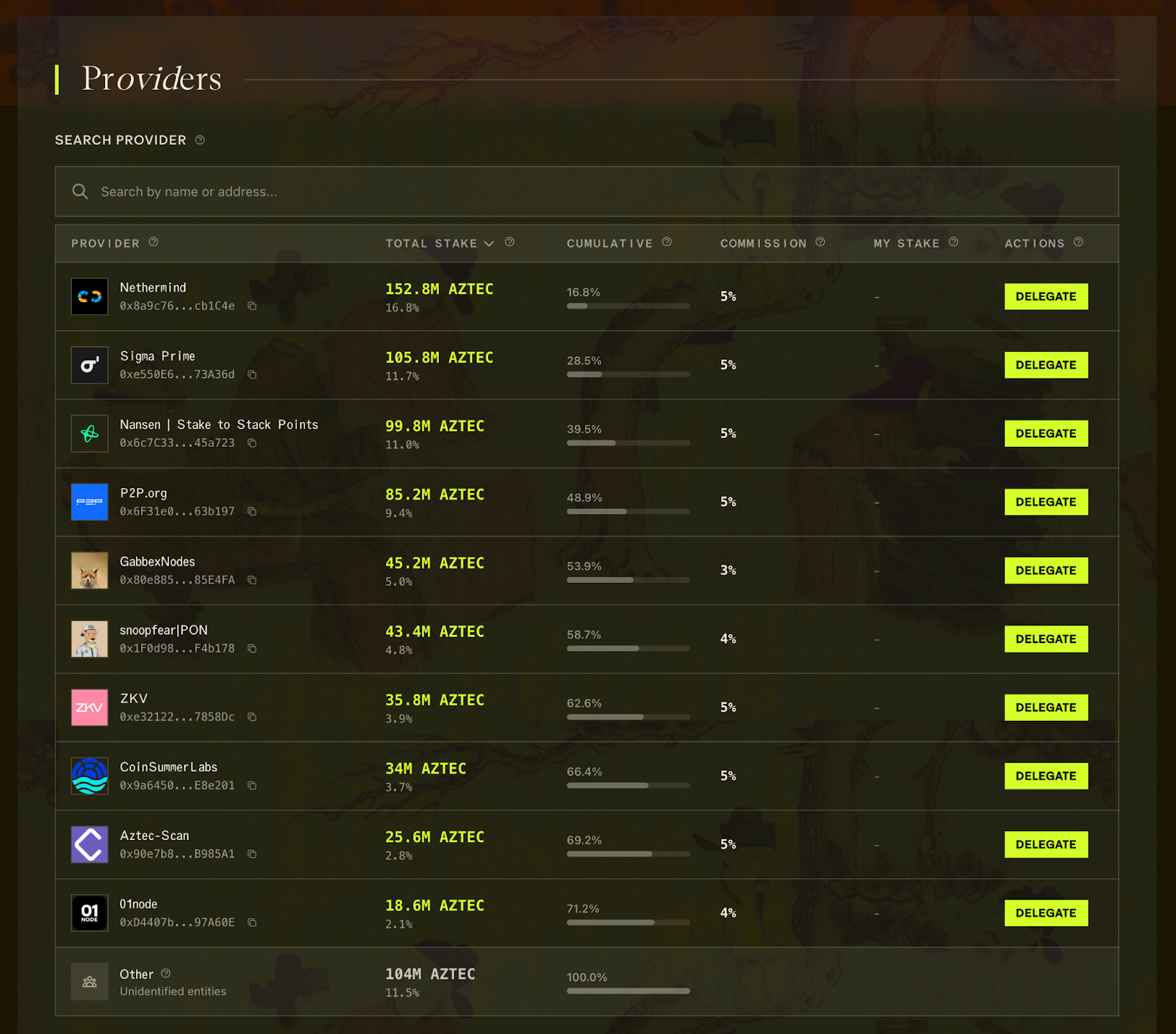
The Ignition Chain launched as a decentralized network from day one. The Aztec Labs and Aztec Foundation teams are not running any sequencers on the network or participating in governance. This is your network.
Anyone who purchased 200k+ tokens in the token sale can stake or delegate their tokens on the staking dashboard. Over 180 operators are now running sequencers, with more joining daily as they enter the sequencer set from the queue. And it's not just sequencers: 50+ provers have joined the permissionless, decentralized prover network to generate block proofs.
These operators span the globe, from solo stakers to data centers, from Australia to Portugal.
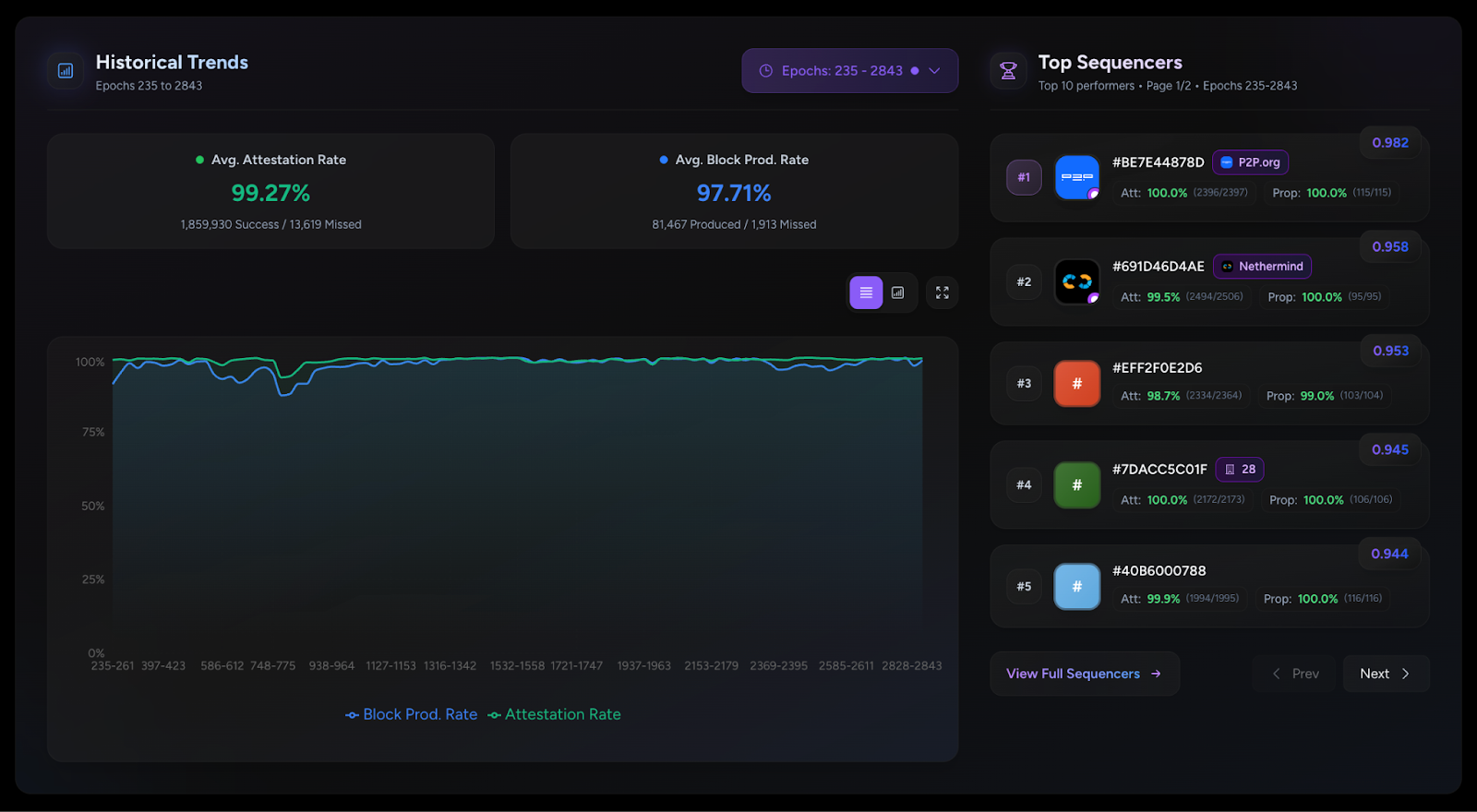
Participating sequencers have maintained a 99%+ attestation rate since network launch, demonstrating strong commitment and network health. Top performers include P2P.org, Nethermind, and ZKV. You can see all block activity and staker performance on the Dashtec dashboard.
On January 26th, 2026, the community passed a governance proposal for TGE. This makes tokens tradable and unlocks the AZTEC/ETH Uniswap pool as early as February 11, 2026. Once that happens, anyone with 200k $AZTEC tokens can run a sequencer or delegate their stake to participate in block rewards.
Here's what you need to run a validator node:
These are accessible specs for most solo stakers. If you've run an Ethereum validator before, you're already well-equipped.
To get started, head to the Aztec docs for step-by-step instructions on setting up your node. You can also join the Discord to connect with other operators, ask questions, and get support from the community. Whether you run your own hardware or delegate to an experienced operator, you're helping build the infrastructure for a privacy-preserving future.
Solo stakers are the beating heart of the Aztec Network. Welcome aboard.
The $AZTEC token sale was the first of its kind, conducted entirely onchain with ~50% of the capital committed coming from the community. The sale was conducted completely onchain to ensure that you have control over your tokens from day one. As we approach the TGE vote, all token sale participants will be able to vote to unlock their tokens and make them tradable.
Immediately following the $AZTEC token sale, tokens could be withdrawn from the sale website into your personal Token Vault smart contracts on the Ethereum mainnet. Right now, token holders are not able to transfer or trade these tokens.
The TGE is a governance vote that decides when to unlock these tokens. If the vote passes, three things happen:
This decision is entirely in the hands of $AZTEC token holders. The Aztec Labs and Aztec Foundation teams, and investors cannot participate in staking or governance for 12 months, which includes the TGE governance proposal. Team and investor tokens will also remain locked for 1 year and then slowly unlock over the next 2 years.
The proposal for TGE is now live, and sequencers are already signaling to bring the proposal to a vote. Once enough sequencers have signaled, anyone who participated in the token sale will be able to connect their Token Vault contract to the governance dashboard to vote. Note, this will require you to stake/unstake and follow the regular 15-day process to withdraw tokens.
If the vote passes, TGE can go live as early as February 12, 2026, at 7am UTC. TGE can be executed by the first person to call the execute function to execute the proposal after the time above.
If you participated in the token sale, you don't have to do anything if you prefer not to vote. If the vote passes, your tokens will become available to trade at TGE. If you want to vote, the process happens in two phases:
Sequencers kick things off by signaling their support. Once 600 out of 1,000 sequencers signal, the proposal moves to a community vote.
After sequencers create the proposal, all Token Vault holders can vote using the voting governance dashboard. Please note that anyone who wants to vote must stake their tokens, locking their tokens for at least 15 days to ensure the proposal can be executed before the voter exits. Once signaling is complete, the timeline is as follows:
Vote Requirements:
Do I need to participate in the vote? No. If you don't vote, your tokens will become available for trading when TGE goes live.
Can I vote if I have less than 200,000 tokens? Yes! Anyone who participated in the token sale can participate in the TGE vote. You'll need to connect your wallet to the governance dashboard to vote.
Is there a withdrawal period for my tokens after I vote? Yes. If you participate in the vote, you will need to withdraw your tokens after voting. Voters can initiate a withdrawal of their tokens immediately after voting, but require a standard 15-day withdrawal period to ensure the vote is executed before voters can exit.
If I have over 200,000 tokens is additional action required to make my tokens tradable after TGE? Yes. If you purchased over 200,000 $AZTEC tokens, you will need to stake your tokens before they become tradable.
What if the vote fails? A new proposal can be submitted. Your tokens remain locked until a successful vote is completed, or the fallback date of November 13, 2026, whichever happens first.
I'm a Genesis sequencer. Does this apply to me? Genesis sequencer tokens cannot be unlocked early. You must wait until November 13, 2026, to withdraw. However, you can still influence the vote by signaling, earn block rewards, and benefit from trading being enabled.
This overview covers the essentials, but the full technical proposal includes contract addresses, code details, and step-by-step instructions for sequencers and advanced users.
Read the complete proposal on the Aztec Forum and join us for the Privacy Rabbit Hole on Discord happening this Thursday, January 22, 2026, at 15:00 UTC.
Follow Aztec on X to stay up to date on the latest developments.
The $AZTEC token sale was conducted entirely onchain to maximize transparency and fair distribution. Next steps for holders are as follows:
The $AZTEC token sale has come to a close– the sale was conducted entirely onchain, and the power is now in your hands. Over 16.7k people participated, with 19,476 ETH raised. A huge thank you to our community and everyone who participated– you all really showed up for privacy. 50% of the capital committed has come from the community of users, testnet operators and creators!
Now that you have your tokens, what’s next? This guide walks you through the next steps leading up to TGE, showing you how to withdraw, stake, and vote with your tokens.
The $AZTEC sale was conducted onchain to ensure that you have control over your own tokens from day 1 (even before tokens become transferable at TGE).
The team has no control over your tokens. You will be self-custodying them in a smart contract known as the Token Vault on the Ethereum mainnet ahead of TGE.
Your Token Vault contract will:
To create and withdraw your tokens to your Token Vault, simply go to the sale website and click on ‘Create Token Vault.’ Any unused ETH from your bids will be returned to your wallet in the process of creating your Token Vault.
If you have 200,000+ tokens, you are eligible to start staking and earning block rewards today.
You can stake by connecting your Token Vault to the staking dashboard, just select a provider to delegate your stake. Alternatively, you can run your own sequencer node.
If your Token Vault holds 200,000+ tokens, you must stake in order to withdraw your tokens after TGE. If your Token Vault holds less than 200,000 tokens, you can withdraw without any additional steps at TGE
Fractional staking for anyone with less than 200,000 tokens is not currently supported, but multiple external projects are already working to offer this in the future.
TGE is triggered by an onchain governance vote, which can happen as early as February 11th, 2026.
At TGE, 100% of tokens from the token sale will be transferable. Only token sale participants and genesis sequencers can participate in the TGE vote, and only tokens purchased in the sale will become transferrable.
Community members discuss potential votes on the governance forum. If the community agrees, sequencers signal to start a vote with their block proposals. Once enough sequencers agree, the vote goes onchain for eligible token holders.
Voting lasts 7 days, requires participation of at least 100,000,000 $AZTEC tokens, and passes if 2/3 vote yes.
Following a successful yes vote, anyone can execute the proposal after a 7-day execution delay, triggering TGE.
At TGE, the following tokens will be 100% unlocked and available for trading:
Join us Thursday, December 11th at 3 pm UTC for the next Discord Town Hall–AMA style on next steps for token holders. Follow Aztec on X to stay up to date on the latest developments.
We invented the math. We wrote the language. Proved the concept and now, we’re opening registration and bidding for the $AZTEC token today, starting at 3 pm CET.
The community-first distribution offers a starting floor price based on a $350 million fully diluted valuation (FDV), representing an approximate 75% discount to the implied network valuation (based on the latest valuation from Aztec Labs’ equity financings). The auction also features per-user participation caps to give community members genuine, bid-clearing opportunities to participate daily through the entirety of the auction.
The token auction portal is live at: sale.aztec.network
We’ve taken the community access that made the 2017 ICO era great and made it even better.
For the past several months, we've worked closely with Uniswap Labs as core contributors on the CCA protocol, a set of smart contracts that challenge traditional token distribution mechanisms to prioritize fair access, permissionless, on-chain access to community members and the general public pre-launch. This means that on day 1 of the unlock, 100% of the community's $AZTEC tokens will be unlocked.
This model is values-aligned with our Core team and addresses the current challenges in token distribution, where retail participants often face unfair disadvantages against whales and institutions that hold large amounts of money.
Early contributors and long-standing community members, including genesis sequencers, OG Aztec Connect users, network operators, and community members, can start bidding today, ahead of the public auction, giving those who are whitelisted a head start and early advantage for competitive pricing. Community members can participate by visiting the token sale site to verify eligibility and mint a soul-bound NFT that confirms participation rights.
To read more about Aztec’s fair-access token sale, visit the economic and technical whitepapers and the token regulatory report.
Discount Price Disclaimer: Any reference to a prior valuation or percentage discount is provided solely to inform potential purchasers of how the initial floor price for the token sale was calculated. Equity financing valuations were determined under specific circumstances that are not comparable to this offering. They do not represent, and should not be relied upon as, the current or future market value of the tokens, nor as an indication of potential returns. The price of tokens may fluctuate substantially, the token may lose its value in part or in full, and purchasers should make independent assessments without reliance on past valuations. No representation or warranty is made that any purchaser will achieve profits or recover the purchase price.
Information for Persons in the UK: This communication is directed only at persons outside the UK. Persons in the UK are not permitted to participate in the token sale and must not act upon this communication.
MiCA Disclaimer: Any crypto-asset marketing communications made from this account have not been reviewed or approved by any competent authority in any Member State of the European Union. Aztec Foundation as the offeror of the crypto-asset is solely responsible for the content of such crypto-asset marketing communications. The Aztec MiCA white paper has been published and is available here. The Aztec Foundation can be contacted at hello@aztec.foundation or +41 41 710 16 70. For more information about the Aztec Foundation, visit https://aztec.foundation.
Every time you swap tokens on Uniswap, deposit into a yield vault, or vote in a DAO, you're broadcasting your moves to the world. Anyone can see what you own, where you trade, how much you invest, and when you move your money.
Tracking and analysis tools like Chainalysis and TRM are already extremely advanced, and will only grow stronger with advances in AI in the coming years. The implications of this are that the ‘pseudo-anonymous’ wallets on Ethereum are quickly becoming linked to real-world identities. This is concerning for protecting your personal privacy, but it’s also a major blocker in bringing institutions on-chain with full compliance for their users.
Until now, your only option was to abandon your favorite apps and move to specialized privacy-focused apps or chains with varying degrees of privacy. You'd lose access to the DeFi ecosystem as you know it now, the liquidity you depend on, and the community you're part of.
What if you could keep using Uniswap, Aave, Yearn, and every other app you love, but with your identity staying private? No switching chains. Just an incognito mode for your existing on-chain life?
If you’ve been following Aztec for a while, you would be right to think about Aztec Connect here, which was hugely popular with $17M TVL and over 100,000 active wallets, but was sunset in 2024 to focus on bringing a general-purpose privacy network to life.
Read on to learn how you’ll be able to import privacy to any L2, using one of the many privacy-focused bridges that are already built.
Aztec is a fully decentralized, privacy-preserving L2 on Ethereum. You can think of Aztec as a private world computer with full end-to-end programmable privacy. A private world computer extends Ethereum to add optional privacy at every level, from identity and transactions to the smart contracts themselves.
On Aztec, every wallet is a smart contract that gives users complete control over which aspects they want to make public or keep private.
Aztec is currently in Testnet, but will have multiple privacy-preserving bridges live for its mainnet launch, unlocking a myriad of privacy preserving features.
Now, several bridges, including Wormhole, TRAIN, and Substance, are connecting Aztec to other chains, adding a privacy layer to the L2s you already use. Think of it as a secure tunnel between you and any DeFi app on Ethereum, Arbitrum, Base, Optimism, or other major chains.
Here's what changes: You can now use any DeFi protocol without revealing your identity. Furthermore, you can also unlock brand new features that take advantage of Aztec’s private smart contracts, like private DAO voting or private compliance checks.
Here's what you can do:
The apps stay where they are. Your liquidity stays where it is. Your community stays where it is. You just get a privacy upgrade.
Let's follow Alice through a real example.
Alice wants to invest $1,000 USDC into a yield vault on Arbitrum without revealing her identity.
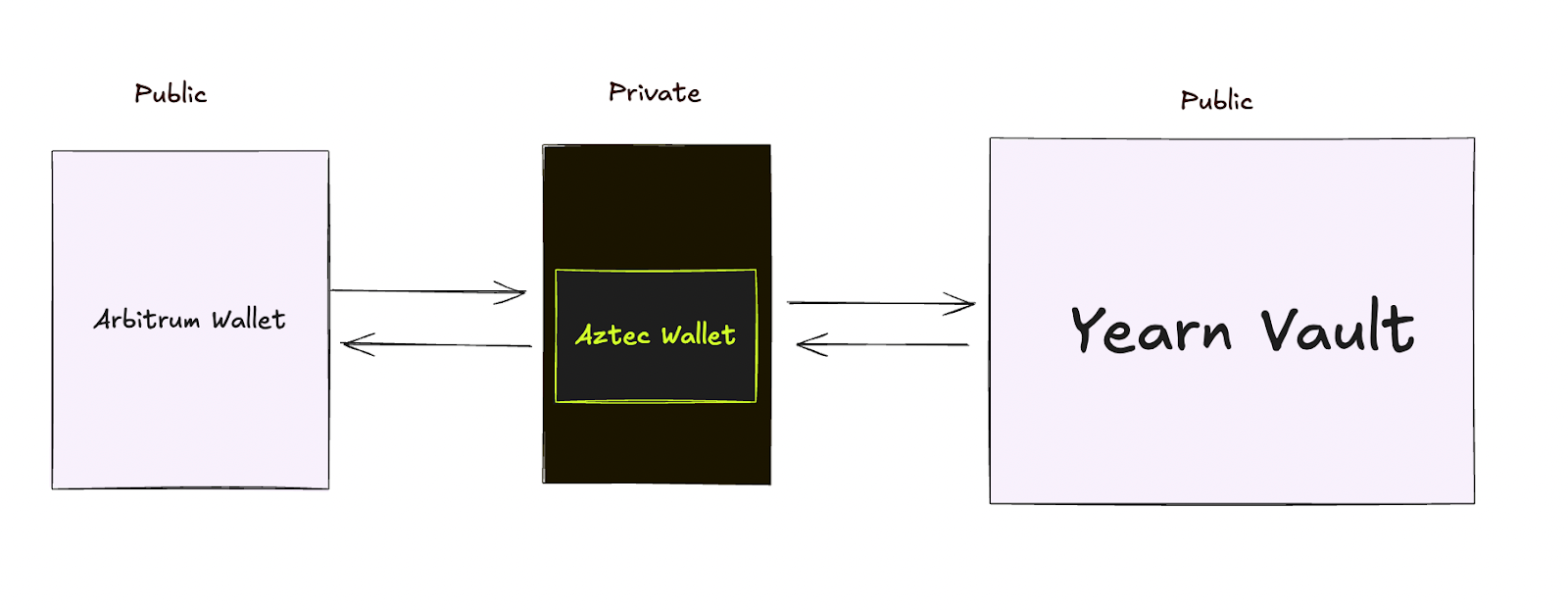
Alice moves her funds into Aztec's privacy layer. This could be done in one click directly in the app that she’s already using if the app has integrated one of the bridges. Think of this like dropping a sealed envelope into a secure mailbox. The funds enter a private space where transactions can't be tracked back to her wallet.
Aztec routes Alice's funds to the Yearn vault on Arbitrum. The vault sees a deposit and issues yield-earning tokens. But there's no way to trace those tokens back to Alice's original wallet. Others can see someone made a deposit, but they have no idea who.
The yield tokens arrive in Alice's private Aztec wallet. She can hold them, trade them privately, or eventually withdraw them, without anyone connecting the dots.
Alice is earning yield on Arbitrum using the exact same vault as everyone else. But while other users broadcast their entire investment strategy, Alice's moves remain private.
The difference looks like this:
Without privacy: "Wallet 0x742d...89ab deposited $5,000 into Yearn vault at 2:47 PM"
With Aztec privacy: "Someone deposited funds into Yearn vault" (but who? from where? how much? unknowable).
In the future, we expect apps to directly integrate Aztec, making this experience seamless for you as a user.
While Aztec is still in Testnet, multiple teams are already building bridges right now in preparation for the mainnet launch.
Projects like Substance Labs, Train, and Wormhole are creating connections between Aztec and major chains like Optimism, Unichain, Solana, and Aptos. This means you'll soon have private access to DeFi across nearly every major ecosystem.
Aztec has also launched a dedicated cross-chain catalyst program to support developers with grants to build additional bridges and apps.
L2s have sometimes received criticism for fragmenting liquidity across chains. Aztec is taking a different approach. Instead, Aztec is bringing privacy to the liquidity that already exists. Your funds stay on Arbitrum, Optimism, Base, wherever the deepest pools and best apps already live. Aztec doesn't compete for liquidity, it adds privacy to existing liquidity.
You can access Uniswap's billions in trading volume. You can tap into Aave's massive lending pools. You can deposit into Yearn's established vaults, all without moving liquidity away from where it's most useful.
We’re rolling out a new approach to how we think about L2s on Ethereum. Rather than forcing users to choose between privacy and access to the best DeFi applications, we’re making privacy a feature you can add to any protocol you're already using. As more bridges go live and applications integrate Aztec directly, using DeFi privately will become as simple as clicking a button—no technical knowledge required, no compromise on the apps and liquidity you depend on.
While Aztec is currently in testnet, the infrastructure is rapidly taking shape. With multiple bridge providers building connections to major chains and a dedicated catalyst program supporting developers, the path to mainnet is clear. Soon, you'll be able to protect your privacy while still participating fully in the Ethereum ecosystem.
If you’re a developer and want a full technical breakdown, check out this post. To stay up to date with the latest updates for network operators, join the Aztec Discord and follow Aztec on X.
Privacy has emerged as a major driver for the crypto industry in 2025. We’ve seen the explosion of Zcash, the Ethereum Foundation’s refocusing of PSE, and the launch of Aztec’s testnet with over 24,000 validators powering the network. Many apps have also emerged to bring private transactions to Ethereum and Solana in various ways, and exciting technologies like ZKPassport that privately bring identity on-chain using Noir have become some of the most talked about developments for ushering in the next big movements to the space.
Underpinning all of these developments is the emerging consensus that without privacy, blockchains will struggle to gain real-world adoption.
Without privacy, institutions can’t bring assets on-chain in a compliant way or conduct complex swaps and trades without revealing their strategies. Without privacy, DeFi remains dominated and controlled by advanced traders who can see all upcoming transactions and manipulate the market. Without privacy, regular people will not want to move their lives on-chain for the entire world to see every detail about their every move.
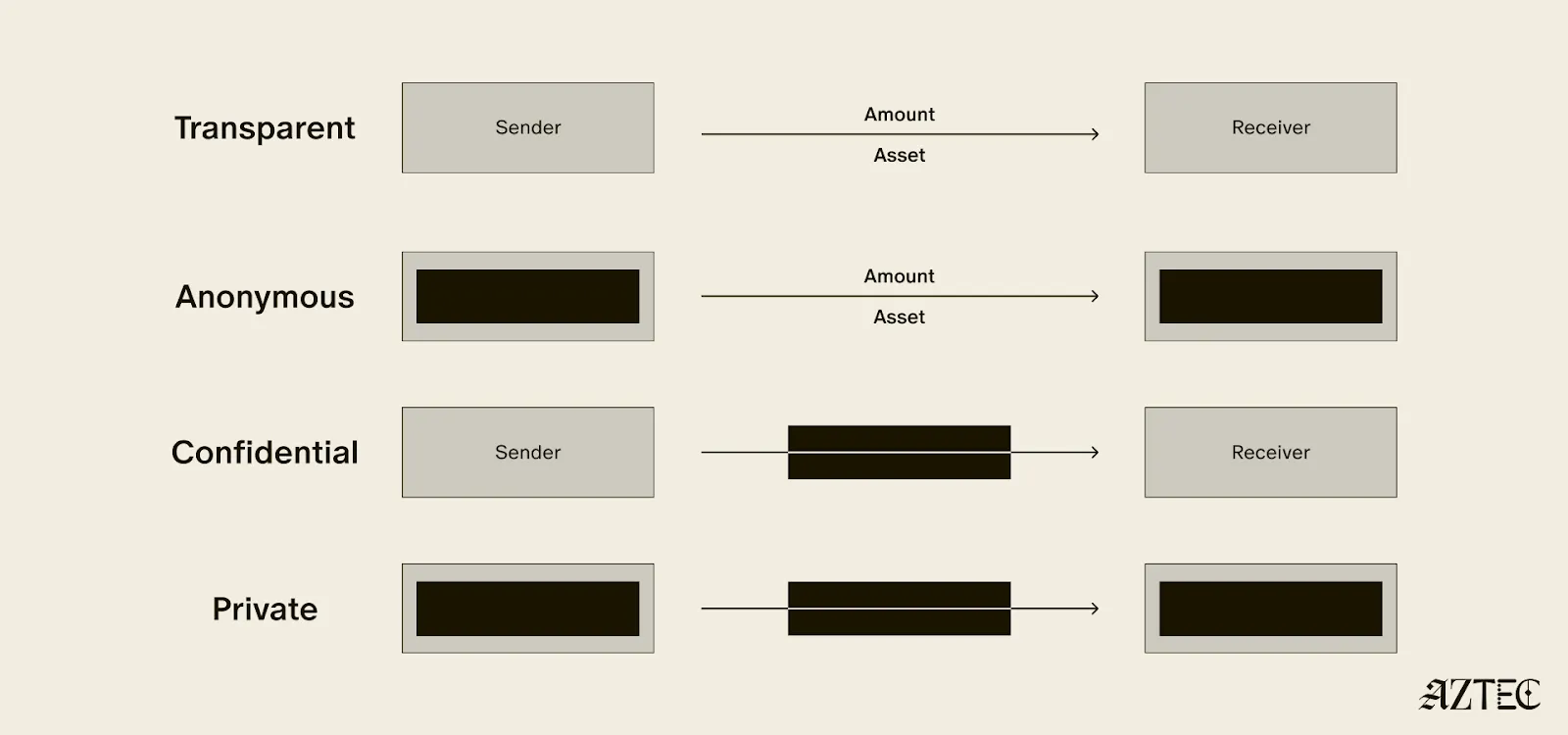
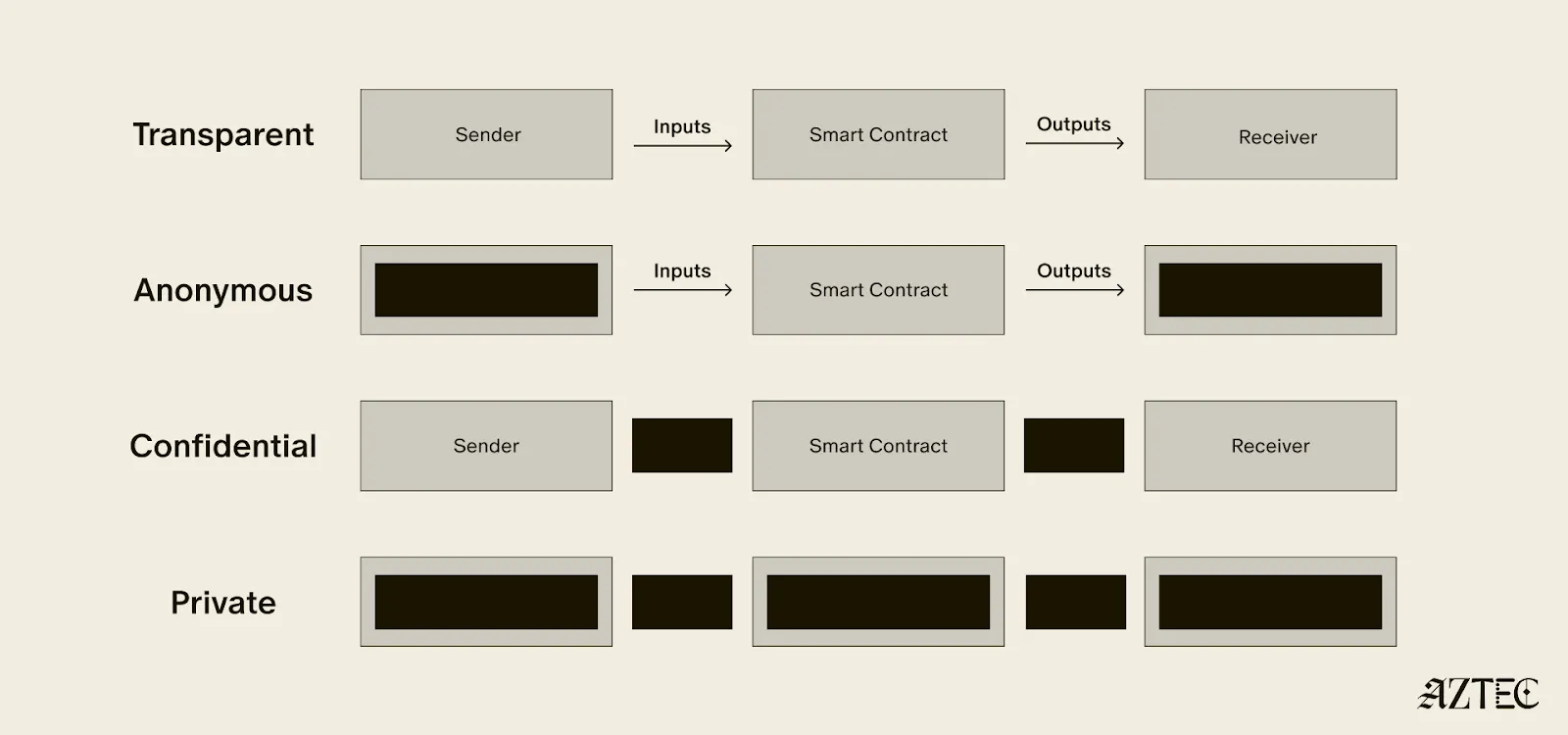
While there's been lots of talk about privacy, few can define it. In this piece we’ll outline the three pillars of privacy and gives you a framework for evaluating the privacy claims of any project.
True privacy rests on three essential pillars: transaction privacy, identity privacy, and computational privacy. It is only when we have all three pillars that we see the emergence of a private world computer.
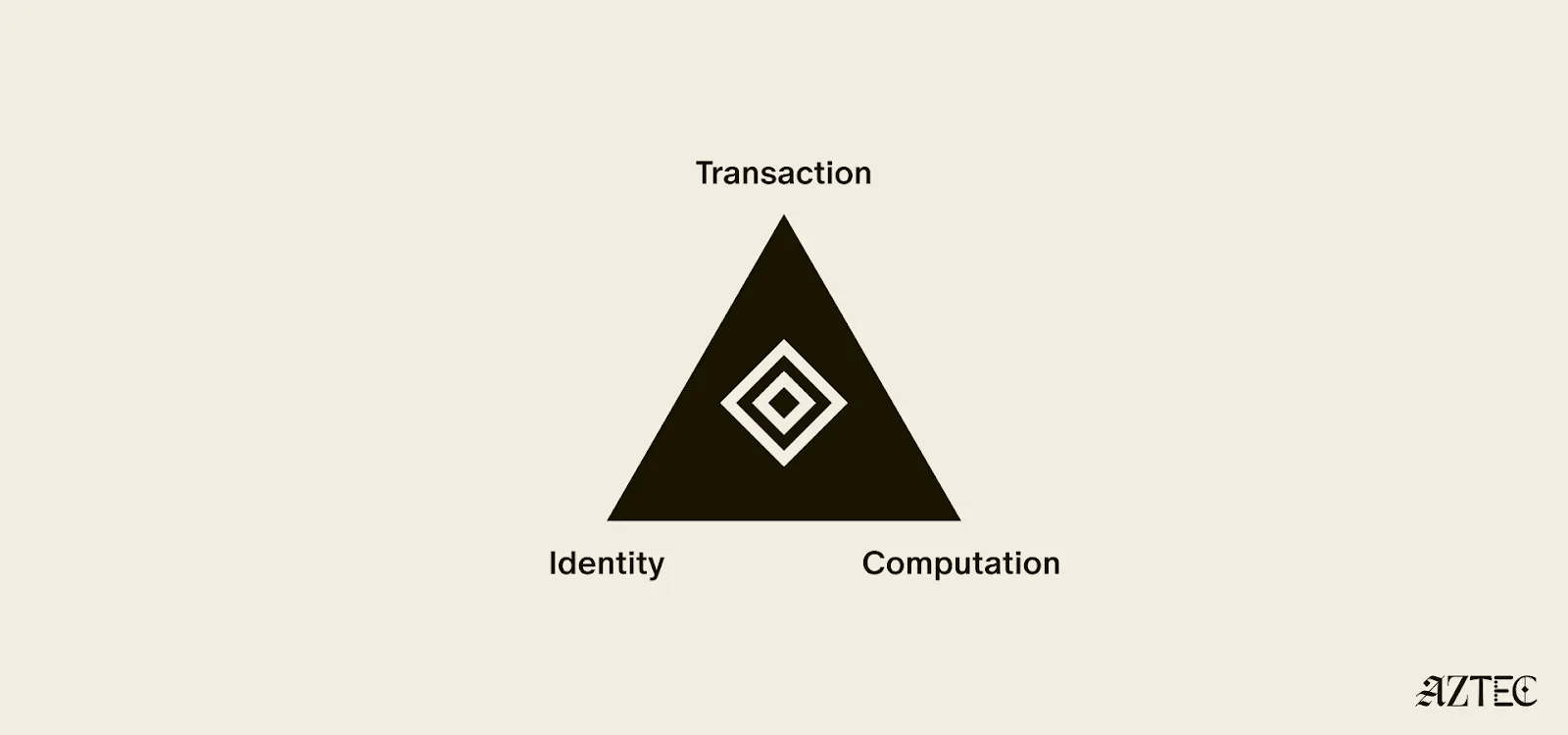
Transaction privacy means that both inputs and outputs are not viewable by anyone other than the intended participants. Inputs include any asset, value, message, or function calldata that is being sent. Outputs include any state changes or transaction effects, or any transaction metadata caused by the transaction. Transaction privacy is often primarily achieved using a UTXO model (like Zcash or Aztec’s private state tree). If a project has only the option for this pillar, it can be said to be confidential, but not private.
Identity privacy means that the identities of those involved are not viewable by anyone other than the intended participants. This includes addresses or accounts and any information about the identity of the participants, such as tx.origin, msg.sender, or linking one’s private account to public accounts. Identity privacy can be achieved in several ways, including client-side proof generation that keeps all user info on the users’ devices. If a project has only the option for this pillar, it can be said to be anonymous, but not private.
Computation privacy means that any activity that happens is not viewable by anyone other than the intended participants. This includes the contract code itself, function execution, contract address, and full callstack privacy. Additionally, any metadata generated by the transaction is able to be appropriately obfuscated (such as transaction effects, events are appropriately padded, inclusion block number are in appropriate sets). Callstack privacy includes which contracts you call, what functions in those contracts you’ve called, what the results of those functions were, any subsequent functions that will be called after, and what the inputs to the function were. A project must have the option for this pillar to do anything privately other than basic transactions.
Bitcoin ushered in a new paradigm of digital money. As a permissionless, peer-to-peer currency and store of value, it changed the way value could be sent around the world and who could participate. Ethereum expanded this vision to bring us the world computer, a decentralized, general-purpose blockchain with programmable smart contracts.
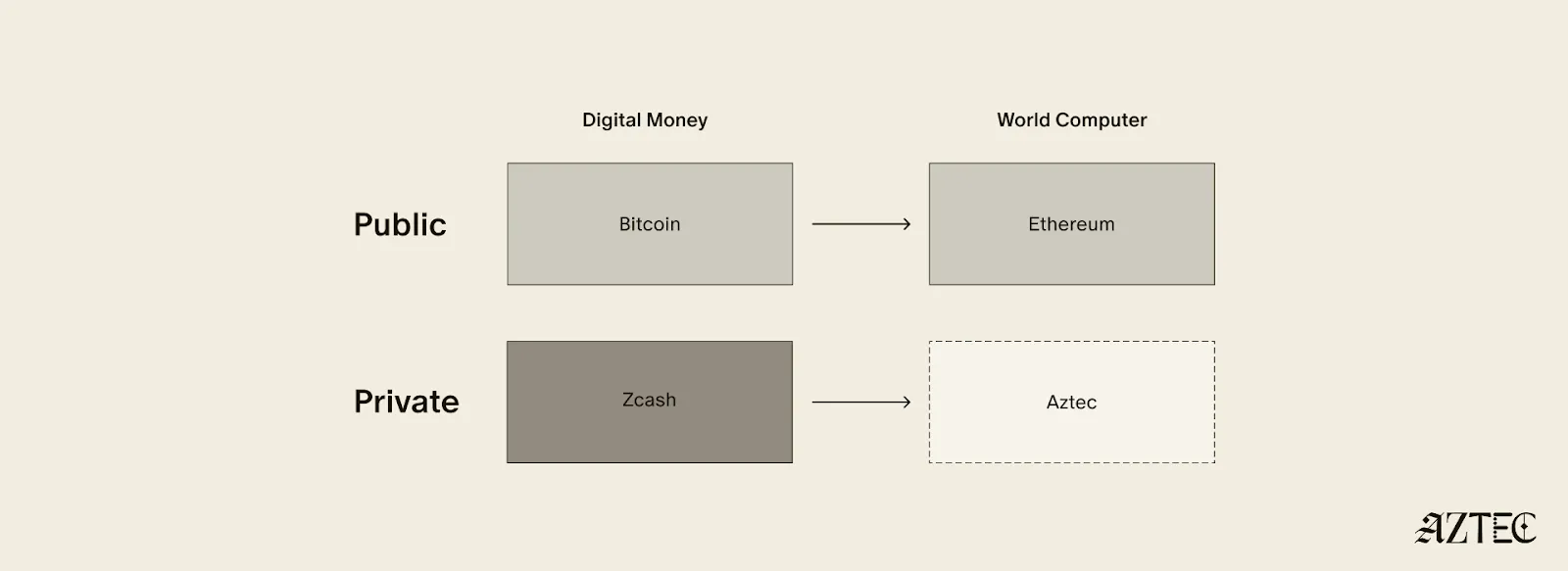
Given the limitations of running a transparent blockchain that exposes all user activity, accounts, and assets, it was clear that adding the option to preserve privacy would unlock many benefits (and more closely resemble real cash). But this was a very challenging problem. Zcash was one of the first to extend Bitcoin’s functionality with optional privacy, unlocking a new privacy-preserving UTXO model for transacting privately. As we’ll see below, many of the current privacy-focused projects are working on similar kinds of private digital money for Ethereum or other chains.
Now, Aztec is bringing us the final missing piece: a private world computer.
A private world computer is fully decentralized, programmable, and permissionless like Ethereum and has optional privacy at every level. In other words, Aztec is extending all the functionality of Ethereum with optional transaction, identity, and computational privacy. This is the only approach that enables fully compliant, decentralized applications to be built that preserve user privacy, a new design space that we see as ushering in the next Renaissance for the space.
Private digital money emerges when you have the first two privacy pillars covered - transactions and identity - but you don’t have the third - computation. Almost all projects today that claim some level of privacy are working on private digital money. This includes everything from privacy pools on Ethereum and L2s to newly emerging payment L1s like Tempo and Arc that are developing various degrees of transaction privacy
When it comes to digital money, privacy exists on a spectrum. If your identity is hidden but your transactions are visible, that's what we call anonymous. If your transactions are hidden but your identity is known, that's confidential. And when both your identity and transactions are protected, that's true privacy. Projects are working on many different approaches to implement this, from PSE to Payy using Noir, the zkDSL built to make it intuitive to build zk applications using familiar Rust-like syntax.
Private digital money is designed to make payments private, but any interaction with more complex smart contracts than a straightforward payment transaction is fully exposed.
What if we also want to build decentralized private apps using smart contracts (usually multiple that talk to each other)? For this, you need all three privacy pillars: transaction, identity, and compute.
If you have these three pillars covered and you have decentralization, you have built a private world computer. Without decentralization, you are vulnerable to censorship, privileged backdoors and inevitable centralized control that can compromise privacy guarantees.
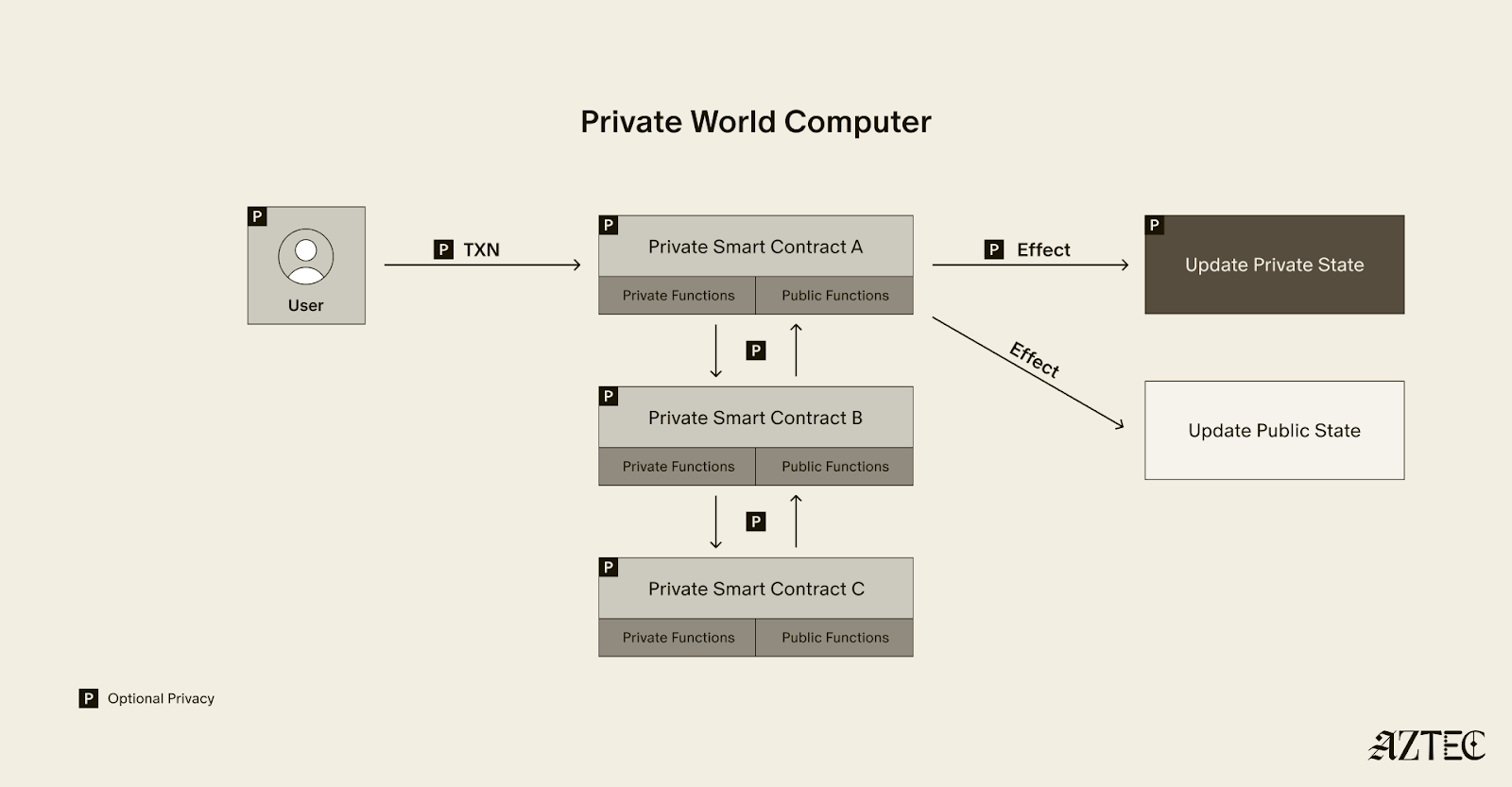
What exactly is a private world computer? A private world computer extends all the functionality of Ethereum with optional privacy at every level, so developers can easily control which aspects they want public or private and users can selectively disclose information. With Aztec, developers can build apps with optional transaction, identity, and compute privacy on a fully decentralized network. Below, we’ll break down the main components of a private world computer.
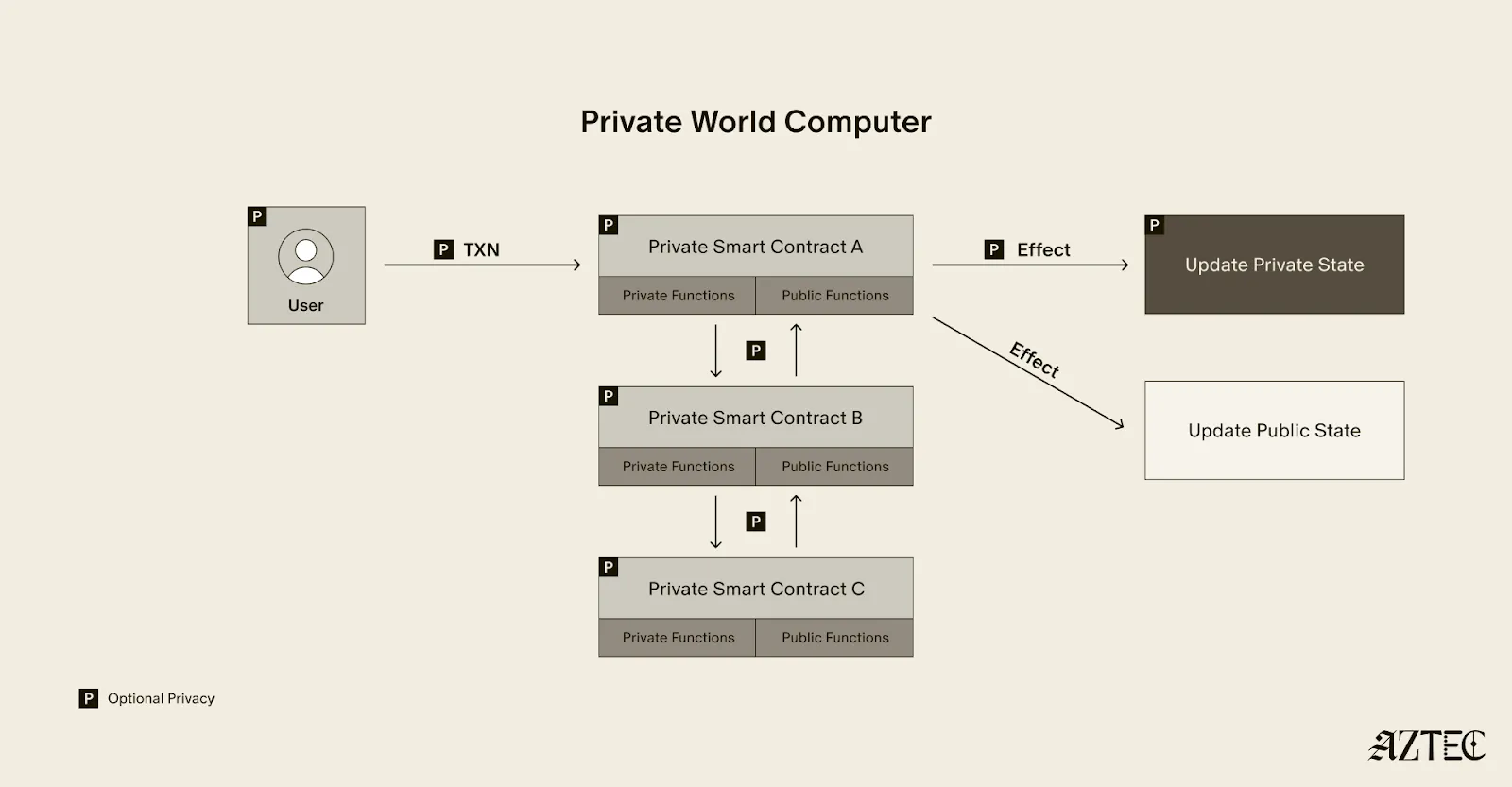
A private world computer is powered by private smart contracts. Private smart contracts have fully optional privacy and also enable seamless public and private function interaction.
Private smart contracts simply extend the functionality of regular smart contracts with added privacy.
As a developer, you can easily designate which functions you want to keep private and which you want to make public. For example, a voting app might allow users to privately cast votes and publicly display the result. Private smart contracts can also interact privately with other smart contracts, without needing to make it public which contracts have interacted.
Transaction: Aztec supports the optionality for fully private inputs, including messages, state, and function calldata. Private state is updated via a private UTXO state tree.
Identity: Using client-side proofs and function execution, Aztec can optionally keep all user info private, including tx.origin and msg.sender for transactions.
Computation: The contract code itself, function execution, and call stack can all be kept private. This includes which contracts you call, what functions in those contracts you’ve called, what the results of those functions were, and what the inputs to the function were.
A decentralized network must be made up of a permissionless network of operators who run the network and decide on upgrades. Aztec is run by a decentralized network of node operators who propose and attest to transactions. Rollup proofs on Aztec are also run by a decentralized prover network that can permissionlessly submit proofs and participate in block rewards. Finally, the Aztec network is governed by the sequencers, who propose, signal, vote, and execute network upgrades.
A private world computer enables the creation of DeFi applications where accounts, transactions, order books, and swaps remain private. Users can protect their trading strategies and positions from public view, preventing front-running and maintaining competitive advantages. Additionally, users can bridge privately into cross-chain DeFi applications, allowing them to participate in DeFi across multiple blockchains while keeping their identity private despite being on an existing transparent blockchain.
This technology makes it possible to bring institutional trading activity on-chain while maintaining the privacy that traditional finance requires. Institutions can privately trade with other institutions globally, without having to touch public markets, enjoying the benefits of blockchain technology such as fast settlement and reduced counterparty risk, without exposing their trading intentions or volumes to the broader market.
Organizations can bring client accounts and assets on-chain while maintaining full compliance. This infrastructure protects on-chain asset trading and settlement strategies, ensuring that sophisticated financial operations remain private. A private world computer also supports private stablecoin issuance and redemption, allowing financial institutions to manage digital currency operations without revealing sensitive business information.
Users have granular control over their privacy settings, allowing them to fine-tune privacy levels for their on-chain identity according to their specific needs. The system enables selective disclosure of on-chain activity, meaning users can choose to reveal certain transactions or holdings to regulators, auditors, or business partners while keeping other information private, meeting compliance requirements.
The shift from transparent blockchains to privacy-preserving infrastructure is the foundation for bringing the next billion users on-chain. Whether you're a developer building the future of private DeFi, an institution exploring compliant on-chain solutions, or simply someone who believes privacy is a fundamental right, now is the time to get involved.
Follow Aztec on X to stay updated on the latest developments in private smart contracts and decentralized privacy technology. Ready to contribute to the network? Run a node and help power the private world computer.
The next Renaissance is here, and it’s being powered by the private world computer.
After eight years of solving impossible problems, the next renaissance is here.
We’re at a major inflection point, with both our tech and our builder community going through growth spurts. The purpose of this rebrand is simple: to draw attention to our full-stack privacy-native network and to elevate the rich community of builders who are creating a thriving ecosystem around it.
For eight years, we’ve been obsessed with solving impossible challenges. We invented new cryptography (Plonk), created an intuitive programming language (Noir), and built the first decentralized network on Ethereum where privacy is native rather than an afterthought.
It wasn't easy. But now, we're finally bringing that powerful network to life. Testnet is live with thousands of active users and projects that were technically impossible before Aztec.
Our community evolution mirrors our technical progress. What started as an intentionally small, highly engaged group of cracked developers is now welcoming waves of developers eager to build applications that mainstream users actually want and need.
A brand is more than aesthetics—it's a mental model that makes Aztec's spirit tangible.
Renaissance means "rebirth"—and that's exactly what happens when developers gain access to privacy-first infrastructure. We're witnessing the emergence of entirely new application categories, business models, and user experiences.
The faces of this renaissance are the builders we serve: the entrepreneurs building privacy-preserving DeFi, the activists building identity systems that protect user privacy, the enterprise architects tokenizing real-world assets, and the game developers creating experiences with hidden information.
This next renaissance isn't just about technology—it's about the ethos behind the build. These aren't just our values. They're the shared DNA of every builder pushing the boundaries of what's possible on Aztec.
Agency: It’s what everyone deserves, and very few truly have: the ability to choose and take action for ourselves. On the Aztec Network, agency is native
Genius: That rare cocktail of existential thirst, extraordinary brilliance, and mind-bending creation. It’s fire that fuels our great leaps forward.
Integrity: It’s the respect and compassion we show each other. Our commitment to attacking the hardest problems first, and the excellence we demand of any solution.
Obsession: That highly concentrated insanity, extreme doggedness, and insatiable devotion that makes us tick. We believe in a different future—and we can make it happen, together.
Just as our technology bridges different eras of cryptographic innovation, our new visual identity draws from multiple periods of human creativity and technological advancement.
Our new wordmark embodies the diversity of our community and the permissionless nature of our network. Each letter was custom-drawn to reflect different pivotal moments in human communication and technological progress.
Together, these letters tell the story of human innovation: each era building on the last, each breakthrough enabling the next renaissance. And now, we're building the infrastructure for the one that's coming.
We evolved our original icon to reflect this new chapter while honoring our foundation. The layered diamond structure tells the story:
The architecture echoes a central plaza—the Roman forum, the Greek agora, the English commons, the American town square—places where people gather, exchange ideas, build relationships, and shape culture. It's a fitting symbol for the infrastructure enabling the next leap in human coordination and creativity.
From the Mughal and Edo periods to the Flemish and Italian Renaissance, our brand imagery draws from different cultures and eras of extraordinary human flourishing—periods when science, commerce, culture and technology converged to create unprecedented leaps forward. These visuals reflect both the universal nature of the Renaissance and the global reach of our network.
But we're not just celebrating the past —we're creating the future: the infrastructure for humanity's next great creative and technological awakening, powered by privacy-native blockchain technology.
Join us to ask questions, learn more and dive into the lore.
Join Our Discord Town Hall. September 4th at 8 AM PT, then every Thursday at 7 AM PT. Come hear directly from our team, ask questions, and connect with other builders who are shaping the future of privacy-first applications.
Take your stance on privacy. Visit the privacy glyph generator to create your custom profile pic and build this new world with us.
Stay Connected. Visit the new website and to stay up-to-date on all things Noir and Aztec, make sure you’re following along on X.
The next renaissance is what you build on Aztec—and we can't wait to see what you'll create.
Aztec’s Public Testnet launched in May 2025.
Since then, we’ve been obsessively working toward our ultimate goal: launching the first fully decentralized privacy-preserving layer-2 (L2) network on Ethereum. This effort has involved a team of over 70 people, including world-renowned cryptographers and builders, with extensive collaboration from the Aztec community.
To make something private is one thing, but to also make it decentralized is another. Privacy is only half of the story. Every component of the Aztec Network will be decentralized from day one because decentralization is the foundation that allows privacy to be enforced by code, not by trust. This includes sequencers, which order and validate transactions, provers, which create privacy-preserving cryptographic proofs, and settlement on Ethereum, which finalizes transactions on the secure Ethereum mainnet to ensure trust and immutability.
Strong progress is being made by the community toward full decentralization. The Aztec Network now includes nearly 1,000 sequencers in its validator set, with 15,000 nodes spread across more than 50 countries on six continents. With this globally distributed network in place, the Aztec Network is ready for users to stress test and challenge its resilience.
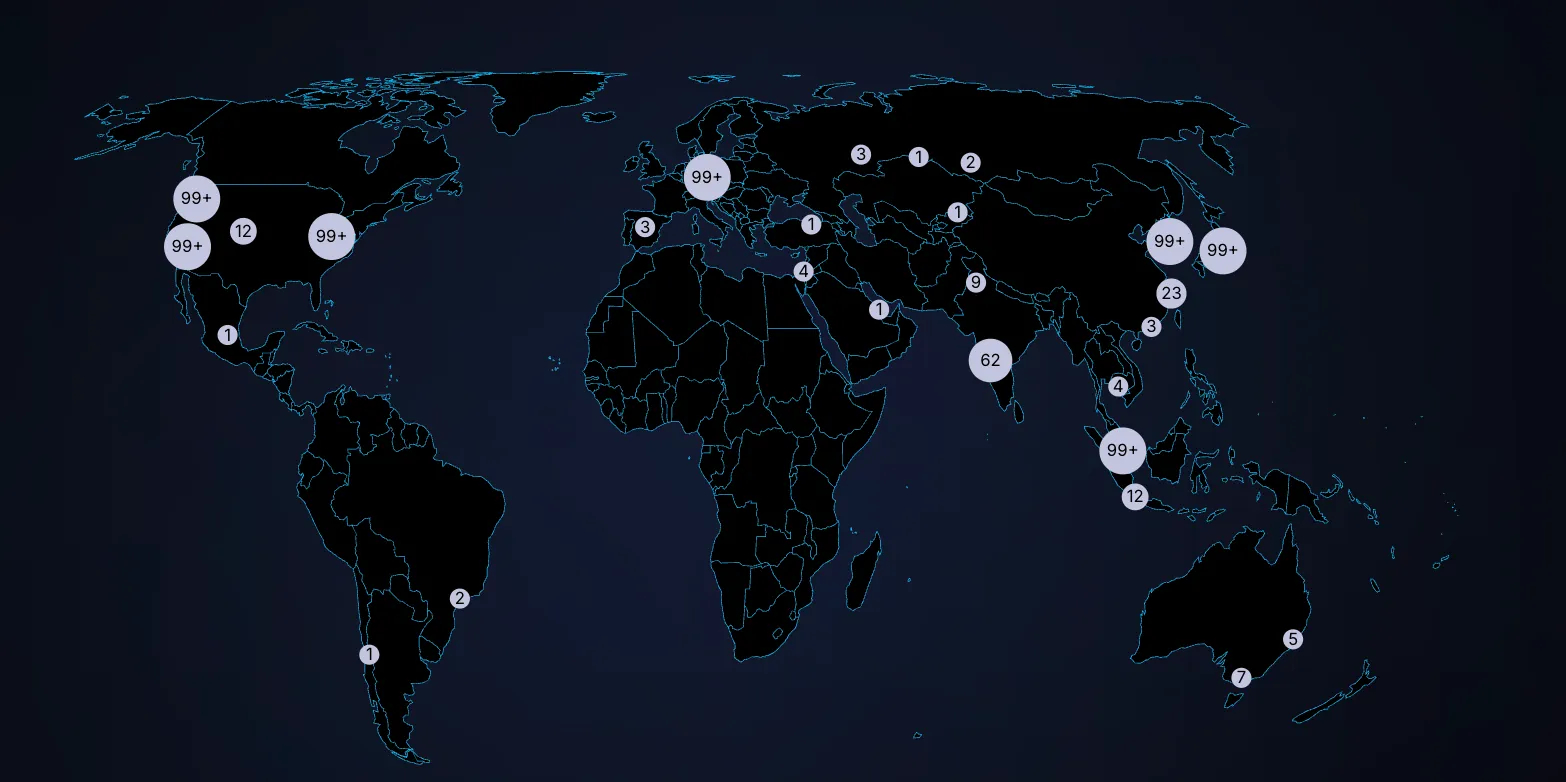
We're now entering a new phase: the Adversarial Testnet. This stage will test the resilience of the Aztec Testnet and its decentralization mechanisms.
The Adversarial Testnet introduces two key features: slashing, which penalizes validators for malicious or negligent behavior in Proof-of-Stake (PoS) networks, and a fully decentralized governance mechanism for protocol upgrades.
This phase will also simulate network attacks to test its ability to recover independently, ensuring it could continue to operate even if the core team and servers disappeared (see more on Vitalik’s “walkaway test” here). It also opens the validator set to more people using ZKPassport, a private identity verification app, to verify their identity online.
The Aztec Network testnet is decentralized, run by a permissionless network of sequencers.
The slashing upgrade tests one of the most fundamental mechanisms for removing inactive or malicious sequencers from the validator set, an essential step toward strengthening decentralization.
Similar to Ethereum, on the Aztec Network, any inactive or malicious sequencers will be slashed and removed from the validator set. Sequencers will be able to slash any validator that makes no attestations for an entire epoch or proposes an invalid block.
Three slashes will result in being removed from the validator set. Sequencers may rejoin the validator set at any time after getting slashed; they just need to rejoin the queue.
In addition to testing network resilience when validators go offline and evaluating the slashing mechanisms, the Adversarial Testnet will also assess the robustness of the network’s decentralized governance during protocol upgrades.
Adversarial Testnet introduces changes to Aztec Network’s governance system.
Sequencers now have an even more central role, as they are the sole actors permitted to deposit assets into the Governance contract.
After the upgrade is defined and the proposed contracts are deployed, sequencers will vote on and implement the upgrade independently, without any involvement from Aztec Labs and/or the Aztec Foundation.
Starting today, you can join the Adversarial Testnet to help battle-test Aztec’s decentralization and security. Anyone can compete in six categories for a chance to win exclusive Aztec swag, be featured on the Aztec X account, and earn a DappNode. The six challenge categories include:
Performance will be tracked using Dashtec, a community-built dashboard that pulls data from publicly available sources. Dashtec displays a weighted score of your validator performance, which may be used to evaluate challenges and award prizes.
The dashboard offers detailed insights into sequencer performance through a stunning UI, allowing users to see exactly who is in the current validator set and providing a block-by-block view of every action taken by sequencers.
To join the validator set and start tracking your performance, click here. Join us on Thursday, July 31, 2025, at 4 pm CET on Discord for a Town Hall to hear more about the challenges and prizes. Who knows, we might even drop some alpha.
To stay up-to-date on all things Noir and Aztec, make sure you’re following along on X.
On May 1st, 2025, Aztec Public Testnet went live.
Within the first 24 hours, over 20k users visited the Aztec Playground and started to send transactions on testnet. Additionally, 10 apps launched live on the testnet, including wallets, block explorers, and private DeFi and NFT marketplaces. Launching a decentralized testnet poses significant challenges, and we’re proud that the network has continued to run despite high levels of congestion that led to slow block production for a period of time.
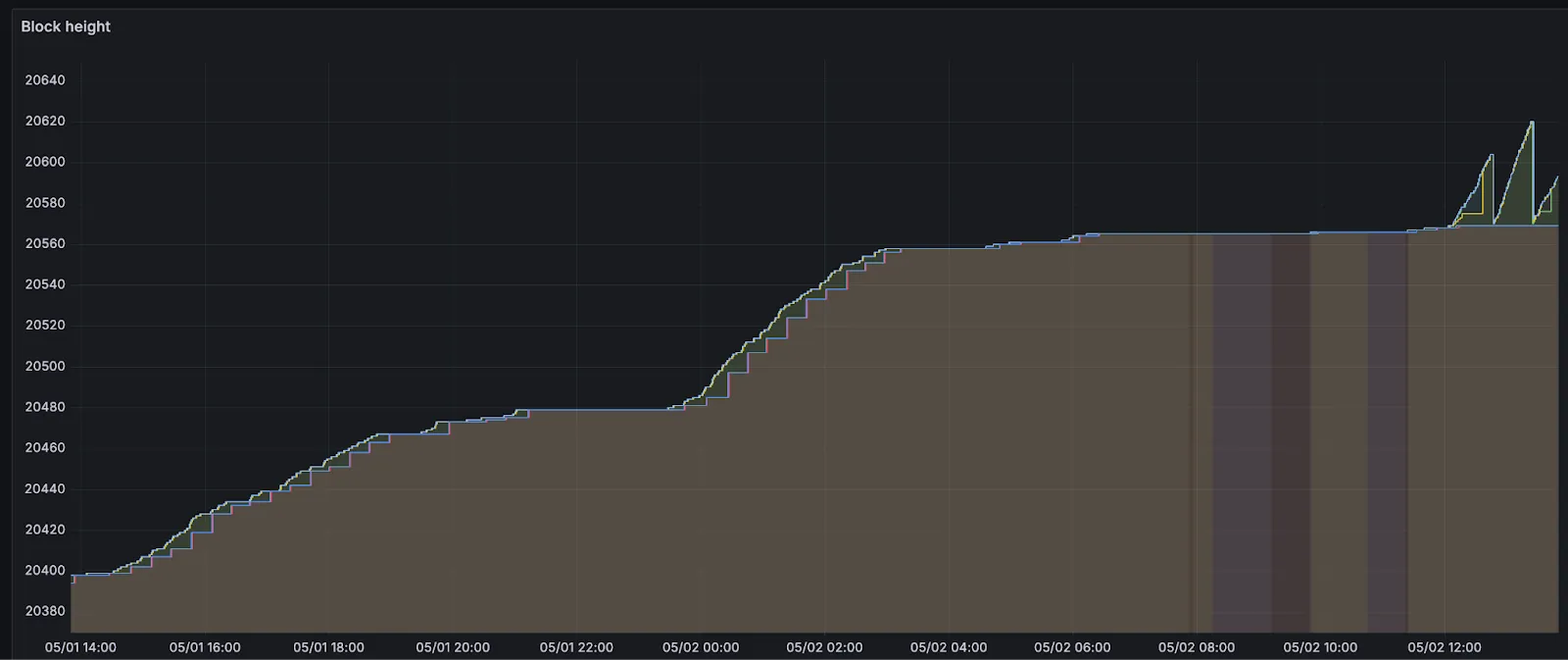
Around 6 hours after announcing the network launch, more than 150 sequencers had joined the validator set to sequence transactions and propose blocks for the network. 500+ additional full nodes were spun up by node operators participating in our Discord community. These sequencers were flooded with over 5k transactions before block production slowed. Let’s dive into why block production slowed down.
On Aztec, an epoch is a group of 32 blocks that are rolled up for settlement on Ethereum. Leading up to the slowdown of block production, there were entire epochs with full blocks (8 transactions, or 0.2TPS) in every slot. The sequencers were building blocks and absorbing the demand for blockspace from users of the Aztec playground, and there was a build up of 100s of pending transactions in sequencer mempools.
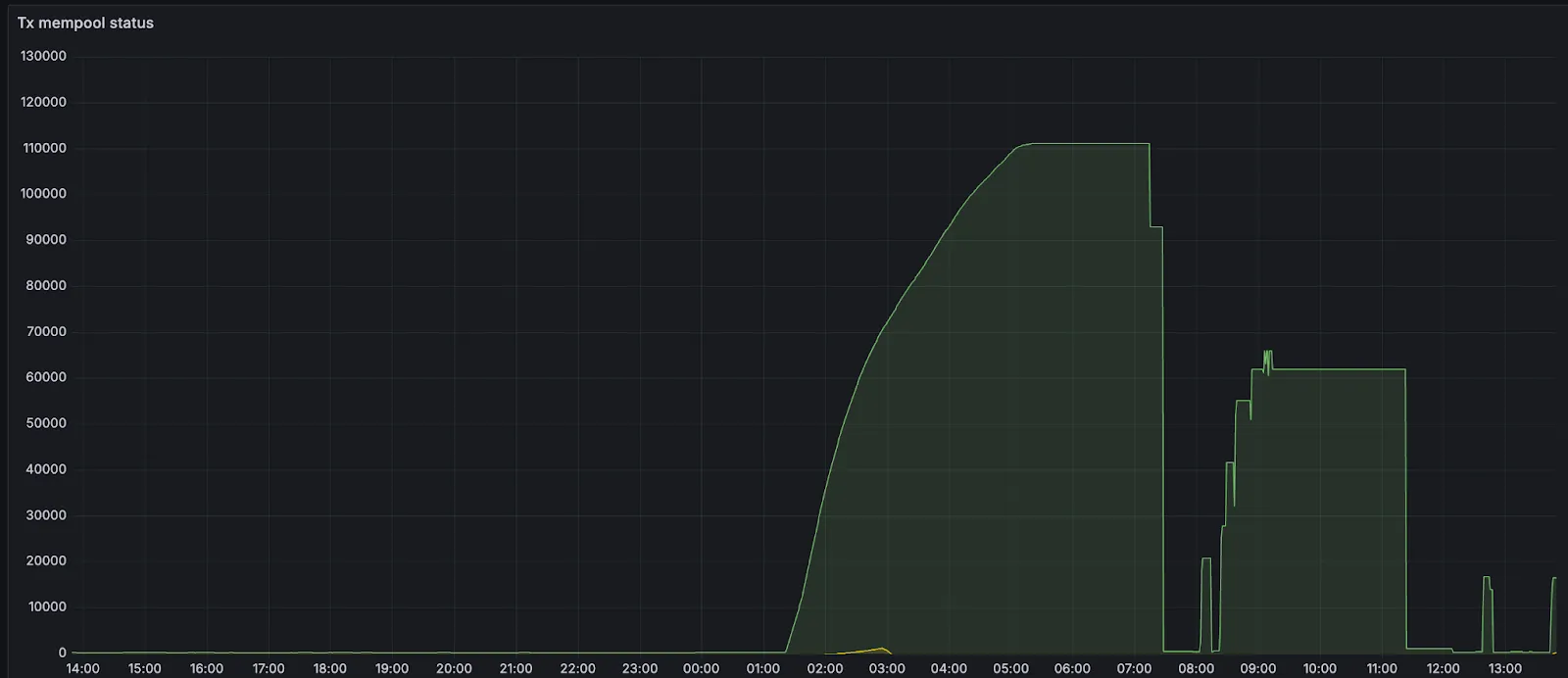
Issues arose when these transactions started to exceed the mempool size, which was configured to hold only 100mb or about 700 transactions.
As many new validators were brought through the funnel and started to come online, the mempools of existing validators (already full at 700 transactions) and new ones (at 0 transactions) diverged significantly. When earlier validators proposed blocks, newer validators didn't have the transactions and could not attest to blocks because the request/response protocol wasn't aggressive enough. When newer validators made proposals, earlier validators didn't have transactions (their mempools were full), so they could not attest to blocks.
New validators then started to build up pending transactions. When validators with full mempools requested missing transactions from peers, they would evict existing transactions from their mempools (mempool is at max memory) based on priority fee. All transactions had default fee settings, so validators were randomly ejecting transactions and were not doing so in lockstep (different validators ejected different transactions). For a little over an hour, the mempools diverged significantly from each other, and block production slowed down to about 20% of the expected rate.
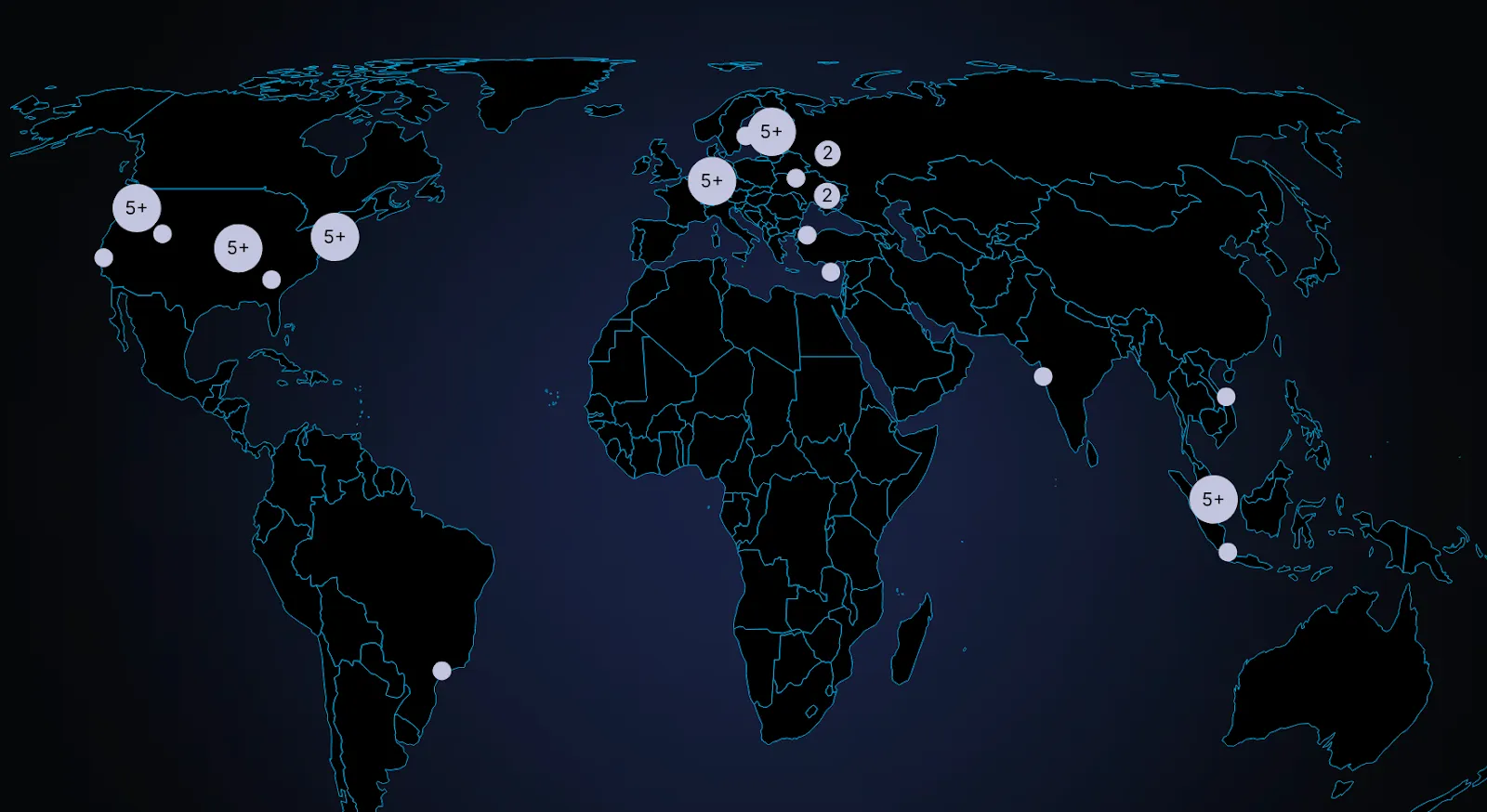
In order to stop the mempool from ejecting transactions, the p2p mempool size was increased. By increasing the mempool size, the likelihood of needing to evict transactions that might soon appear in proposals is reduced. This increases the chances that sequencers already have the necessary transactions locally when they receive a block proposal. As a result, more validators are able to attest to proposals, allowing blocks to be finalized more reliably. Once blocks are included on L1, their transactions are evicted from the mempool. So over time, as more blocks are finalized and transactions are mined, the mempool naturally shrinks and the network will recover on its own.
If you are interested in running a sequencer node visit the sequencer page. Stay up-to-date on Noir and Aztec by following Noir and Aztec on X.
It’s been a big year for Noir, the universal language for zero-knowledge.
We made things official with GitHub and became an official coding language, cozied up with Vitalik at the inaugural NoirCon0 in Thailand, and now we’re making zero-knowledge proofs more accessible and powerful for developers worldwide with the Noir 1.0 pre-release.
Noir is an open-source, proving-system-agnostic language designed specifically for zk applications, which marks a significant advancement in zk app development.
Noir has quickly emerged as a developer favorite in the zk space, boasting over 600 GitHub projects, 900 stars, and 2,000+ VS Code extension installations. Its growing popularity stems from an emphasis on developer experience, featuring an intuitive Rust-inspired syntax that makes zk programming more accessible than ever. Leading projects like zkEmail, zkPassport, zkLogin, and Aztec Network are already leveraging Noir's capabilities to create innovative zk applications.
Noir was built with a clear vision: to be the most developer-friendly and versatile language for zero-knowledge applications. As a public good, it empowers developers to build on-chain and off-chain applications with confidence. Its proving system agnostic design means you have complete flexibility to use Noir with supported proving systems like Barretenberg, Halo2, Plonky2, or Groth16.
With privacy baked into Noir as a default, developers have full control over which aspects they want to expose with a simple pub keyword. No underlying knowledge of cryptography or complicated mathematics is required, and we’re starting to see more and more developers turn to Noir to build their privacy-focused applications such as AnonCast.
The 1.0 pre-release brings a comprehensive set of language features that make writing ZK circuits feel natural and intuitive:
We’ve already seen many incredible libraries developed by the community, but Noir also ships with its extensive library that includes:
The feedback is in – developers love Noir!
We’ve been relentlessly focused on delivering a world-class developer experience with an emphasis on providing tooling to speed up and simplify the development process.
Noir supports integration with different proving systems to cater for varying development needs in e.g. proving times, memory footprint, proof sizes for different applications:
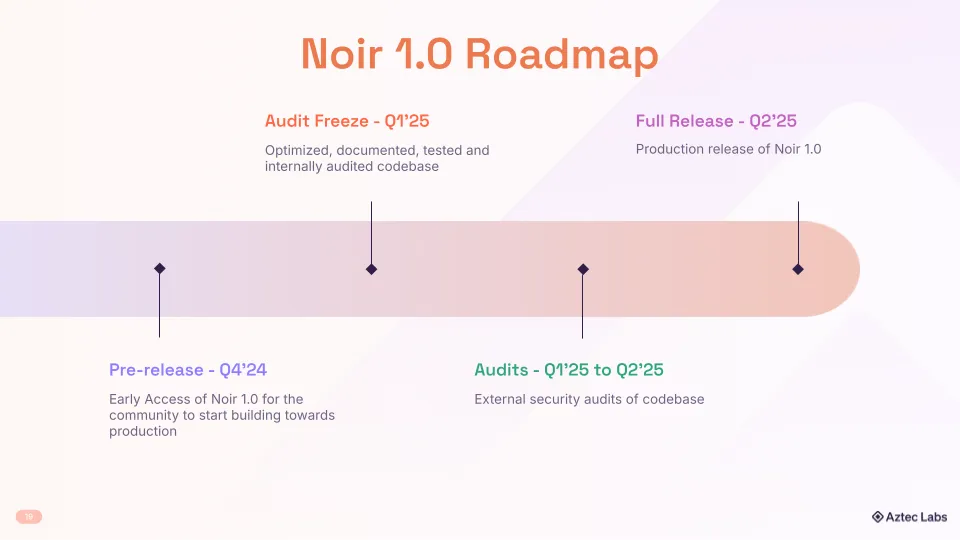
This pre-release marks the beginning of Noir's journey to 1.0 and we're committed to ensuring stability and security through comprehensive audits before the full release.
Noir is more than just a language—it's a community-driven effort to make zero-knowledge proofs accessible to every developer. We invite you to:
The future of ZK development is here, and it speaks Noir.
Since Aztec's launch seven years ago, we’ve been on a mission to solve one of the biggest barriers to mass blockchain adoption – privacy.
The journey towards building a fully decentralized, privacy-preserving network is a massive undertaking. From the beginning, we’ve been committed to building in the open and involving our community in major decisions through discussions, grants, and ongoing builder competitions.
Our team and community have worked tirelessly to bring this vision to life, and their efforts have paid off. In August of this year, we delivered the first major milestone towards our vision by unveiling a live Aztec Devnet. Many puzzle pieces came together to reach this stage, including developing a novel proving system (Honk), creating an intuitive zk programming language (Noir), and building a private execution environment (PXE) to generate private, client-side proofs.
Together, these components unlock one of the most powerful missing pieces for protecting user data on blockchains: client-side zk proof generation. Developers don’t need to struggle to implement these privacy features - they can simply specify which functions will run privately and which will run publicly.
But privacy is only half of the story. We are committed to decentralizing every aspect of the network, from sequencers and provers all the way to settlement on Ethereum. In September, we launched an early Provernet, a decentralized network of provers generating zk proofs for Aztec transactions. We were amazed by the passion of the participants to generate efficient proofs and contribute towards a decentralized future for the network.
Now imagine a world where both of these elements, privacy and decentralization, are seamlessly brought together. Where developers can write programs that protect user data but take full advantage of a trustless, permissionless system – all backed by the security of Ethereum.
This is what we’re working towards, and this product roadmap is how we get there.
Join us Thursday, October 10th at 9 a.m. PST on X to hear more about our road to mainnet from our Co-Founders, Zac Williamson and Joe Andrews. Stay updated on all things Noir and Aztec by following Noir and Aztec on X, and join the Aztec developer community on Discord.
After 7 years of building in the open, last month we announced that Devnet is now live. This marked a huge milestone for Aztec and the Ethereum community by enabling private, client-side smart contract execution with robust public verifiability.
To celebrate we launched Alpha Build, a series of three developer sprints with up to US$100,000 in prizes and the opportunity to deploy on the Aztec for the first time. The first sprint, Alpha Build 1, focused on payments, wallets, programmable accounts, and fees. It garnered 50 participants, 6 teams, and a total of 13 amazing projects, ranging from wallets using Ethereum signatures to cloud based wallet features and beyond.
Starting October 8th - October 29th, 2024, the second sprint, Alpha Build 2 (AB2), will focus on identity and social. In this developer sprint, we’re seeking real-world use cases for privacy-preserving identity verification. We want to explore applications of zero-knowledge (ZK) technology, including innovative uses that integrate email verification and social attestations, as well as a modular approach to creating privacy-first applications.
Select one idea from the list below or suggest your own to the Aztec Team before beginning the challenge. Please detail your choice in your project’s ReadMe, or you can utilize an existing zkEmail circuit in Noir.
Some ideas to help get you started:
See the full list of zkEmail's project ideas for more inspiration on novel ways in which email can be used for verification.
For this challenge, we’re looking for 3 things:
Some ideas to help you get started:
The evaluation criteria for AB2 emphasize innovation in privacy preservation, assessing how effectively the proposed solution safeguards user data while maintaining practical viability, including proving times and transaction fees.
The Aztec Team will also account for potential impact on the Aztec ecosystem and how well the solution leverages its unique features, along with demonstrating tangible real-world applications and benefits.
Solutions that excel in these areas will be prioritized for their ability to drive meaningful advancements in privacy and utility within Aztec.
Don’t miss your chance to deploy on the Aztec Network for the first time and for a piece of the US$100,000 prize pool.
To get started, fill out the Alpha Build Application. We will review applications and, if selected, invite you to join a private Discord channel for Alpha Build. Join us October 3, 2024, at 11:00 a.m. ET on X to hear more about Alpha Build 2 from our President and Co-Founder, Joe Andrews as we explore challenges, themes, and innovative ideas.
Stay updated on all things Noir and Aztec by following Noir and Aztec on X, and join the Aztec developer community on Discord.
Ariel Gabizon, a distinguished cryptographer, coauthor of PLONK, and pioneer of zero-knowledge (ZK) technology, has rejoined Aztec Labs as its Chief Scientist.
Ariel brings over 14 years of experience in mathematics and has played a key role in major advancements in ZK technology. He began with a PhD in Theoretical Computer Science from the Weizmann Institute. During his postdoctoral tenure, a serendipitous encounter with the Bitcoin whitepaper ignited his passion for applied cryptography.
This led him to join Eli Ben-Sasson's lab, where he made significant contributions to the early development of STARKs when they were known as probabilistically checkable proofs (PCPs). He was involved in the first deployment of ZK technology at Zcash and coauthored two pivotal papers that made SNARK setups practical and viable.
In addition to his groundbreaking work on the PLONK paper, co-authored with Zachary Williamson, Ariel also helped discover a crucial counterfeiting vulnerability stemming from the underlying zk-SNARK originally used by Zcash. Since then, he has been advancing the state of the art in polynomial commitment schemes (SHPLONK, FFLONK), lookup protocols (Plookup,cq) and folding schemes (ProtoGalaxy).
With Devnet now live and private, client-side smart contract execution with public verifiability possible, Ariel is rejoining us at a pivotal moment for Aztec, our upcoming privacy-first L2 on Ethereum. His expertise and vision will be vital in continuing to drive our efforts to build a more private, secure, and efficient blockchain ecosystem. As Chief Scientist, Ariel will spearhead our research and development efforts, focusing on enhancing the privacy and scalability of Aztec. Ariel’s expertise will not only bolster our existing work but pave the way for innovative advancements in ZK technology. You can read more about the work Ariel is doing at Aztec via his recently published paper, Private Proofs of Stack and Contract Execution Using Protogalaxy.
Ariel is speaking at the Verifiable Summit during Warsaw Blockchain Week on September 4th, 2024. This event will provide a platform for Ariel to discuss recent progress on Fast Fourier Transforms from the Galois FFT and circle STARK papers. Get your discounted ticket using FRENSOFAZTEC.
We are confident that Ariel’s experience and expertise in mathematics, cryptography and ZK technology will propel us to new heights. We invite our community to follow us on X for regular updates.